
SKC™ Secure KMIP Client
SKC™ enables the easy addition of KMIP based interoperable key management to your application.
- Royalty Free License
- Available for Windows™ | Linux™ | Linux™ ARM (with source license)
Please contact our sales team if you have any questions.
What's New
- Many bug fixes and optimizations.
- Java JNI and Python language bindings
- GCC v5+ compiler support.
- ARM processor Support (with source license).
The SKC™ SDK provides a full implementation of the OASIS KMIP 1.0, 1.1, 1.2, 1.3, 1.4, 2.0, 2.1 and 3.0 draft standard.
- Layered, Interface Based C/C++ API
- Java JNI and Python language bindings
- PKCS11 v2.40 and v3.0 compliant C based API
- Full KMIP Client Implementation (TTLV, XML and JSON).
- Single API for All protocol flavors (TTLV, XML, and JSON)
- Extensive Protocol Logging (TTLV, XML and JSON)
- IPv4/IPv6 support.
- Suite B crypto support.
- Many New Examples (we are always adding more)
- High level crypto API
- Cross Platform/Single Codebase - Windows and Linux x86 - ARM (with source license)
- Standards Compliant (see the Standards and Conformance tabs)
- Support for KMIP put and notify.
Interoperability
P6R is committed to ensuring interoperability of its KMIP client SDK with all KMIP servers and we are continually working with server vendors to ensure interoperability. SKC has been tested and works with the following KMIP servers:- Cryptsoft C KMIP Server
- Cryptsoft Java KMIP Server
- Dell KMIP Server
- Fornetix Key Orchestration Server
- Hancom Secure KeyManager
- KeyNexus Universal Key Manager
- Kryptus kNET HSM
- Microfocus ESKM Server (formerly HPE)
- IBM SKLM Server
- QuintessenceLabs qCrypt Server
- SafeNet KeySecure Server
- Thales KeyAuthority KMIP Server
- Townsend Security Alliance Key Manager
- Unbound UKC Server
- Utimaco KeyServer
- Vormetric Data Security Manager KMIP Server
- StorMagic SvKMS
Layered API
The SKC™ SDK provides several different layers of abstraction, each building on the previous, enabling developers to use whichever layer or layers best suit their needs.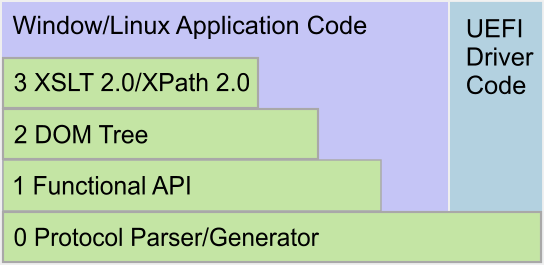
Layer 0 - Protocol Parser/Generator
This layer of the API provides full binary KMIP protocol message parsing and message generation. It is used to parse existing (already received) KMIP protocol messages or generate KMIP protocol message to be sent.Layer 1 - Functional API
Layer 1 implements a slight higher level API that is more functional in nature, providing the base functionality for the various KMIP protocol interactions (connect to the server, create key, delete key, etc).Layer 2 - DOM Tree
Layer 2 provides our DOM-tree API. Our DOM-tree has been enhanced to efficiently support binary data types. Utilizing a plugin it populates the DOM-tree with KMIP messages using the layer 1 APIs. Since a KMIP message is essentially a tree of nested structures this translation is straight forward. Once in the DOM tree, the data can be output in any supported format (XML, JSON, JsonML and a KMIP binary messages).Layer 3 - XSLT/XPATH
This layer uses P6R's XSLT 2.0 and XPath 2.0 components. These components are now able to interact with the KMIP binary data in the DOM-tree, allowing it to be search, transformed, modified, etc using standard XSLT and XPath. For example, XSLT could be used to take just out part of a KMIP message, create a new message, or transform the entire message into yet another format (eg. SOAP or XML-RPC).Full Client Implementation
The SKC™ SDK implements:- TTLV (Tag, Type, Length, Value) over SSL/TLS
- TTLV over HTTPS
- XML over HTTPS
- JSON over HTTPS
KMIP 1.0 Operations Supported (both synchronous and asynchronous)
Create, Create Key Pair, Register, Re-key, Derive Key, Certify, Re-certify, Locate, Check, Get, Get Attributes, Get Attribute List, Add Attribute, Modify Attribute, Delete Attribute, Obtain Lease, Get Usage Allocation, Activate, Revoke, Destroy, Archive, Recover, Validate, Query (synch only), Cancel, Poll, and Server to Client operations: Notify, Put.KMIP 1.1 Operations Supported (both synchronous and asynchronous):
Create, Create Key Pair, Register, Re-key, Derive Key, Certify, Re-certify, Locate, Check, Get, Get Attributes Get Attribute List, Add Attribute, Modify Attribute, Delete Attribute, Obtain Lease, Get Usage Allocation, Activate, Revoke, Destroy, Archive, Recover, Validate, Query (synch only), Cancel, Poll, Re-key Key Pair, Discover Versions (synch only), and Server to Client operations: Notify, Put.KMIP 1.2 Operations Supported (both synchronous and asynchronous):
Create, Create Key Pair, Register, Re-key, Derive Key, Certify, Re-certify, Locate, Check, Get, Get Attributes Get Attribute List, Add Attribute, Modify Attribute, Delete Attribute, Obtain Lease, Get Usage Allocation, Activate, Revoke, Destroy, Archive, Recover, Validate, Query (synch only), Cancel, Poll, Re-key Key Pair, Discover Versions (synch only), Encrypt, Decrypt, Sign, Signature Verify, MAC, MAC Verify, RNG Retrieve, RNG Seed, Hash, Create Split Key, Join Split Key, and Server to Client operations: Notify, Put.KMIP 1.3 Operations Supported (both synchronous and asynchronous):
Create, Create Key Pair, Register, Re-key, Derive Key, Certify, Re-certify, Locate (extended), Check, Get, Get Attributes Get Attribute List, Add Attribute, Modify Attribute, Delete Attribute, Obtain Lease, Get Usage Allocation, Activate, Revoke, Destroy, Archive, Recover, Validate, Query (synch only), Cancel, Poll, Re-key Key Pair, Discover Versions (synch only), Encrypt (streaming/non-streaming), Decrypt (streaming/non-streaming), Sign (streaming/non-streaming), Signature Verify (streaming/non-streaming), MAC (streaming/non-streaming), MAC Verify (streaming/non-streaming), RNG Retrieve, RNG Seed, Hash (streaming/non-streaming), Create Split Key, Join Split Key, and Server to Client operations: Notify, Put, Discover Versions (new), Query (new)KMIP 1.4 Operations Supported (both synchronous and asynchronous):
Create, Create Key Pair, Register, Re-key, Re-key Key Pair, Derive Key, Certify, Re-certify, Locate, Check, Get, Get Attributes, Get Attribute List, Add Attribute, Modify Attribute, Delete Attribute, Obtain Lease, Get Usage Allocation, Activate, Revoke, Destroy, Archive, Recover, Validate, Query (synch only), Discover Versions (synch only), Cancel, Poll, Encrypt (streaming/non-streaming), Decrypt (streaming/non-streaming), Sign (streaming/non-streaming), Signature Verify (streaming/non-streaming), MAC (streaming/non-streaming), MAC Verify (streaming/non-streaming), RNG Retrieve, RNG Seed, Hash (streaming/non-streaming), Create Split Key, Join Split Key, Export, import, and Server to Client operations: Notify, Put, Discover Versions, QueryObjects Supported: Certificate, Opaque Object, PGP Key, Private Key, Public Key, Secret Data, Split Key, Symmetric Key
KMIP 2.0 Operations Supported (both synchronous and asynchronous):
Create, Create Key Pair, Register, Re-key, Re-key Key Pair, Derive Key, Certify, Re-certify, Locate, Check, Get, Get Attributes, Get Attribute List, Add Attribute, Modify Attribute, Delete Attribute, Obtain Lease, Get Usage Allocation, Activate, Revoke, Destroy, Archive, Recover, Validate, Query (synch only), Discover Versions (synch only), Cancel, Poll, Encrypt (streaming/non-streaming), Decrypt (streaming/non-streaming), Sign (streaming/non-streaming), Signature Verify (streaming/non-streaming), MAC (streaming/non-streaming), MAC Verify (streaming/non-streaming), RNG Retrieve, RNG Seed, Hash (streaming/non-streaming), Create Split Key, Join Split Key, Export, Import, Adjust Attribute, Delegated Login, Interop, Log, Login, Logout, PKCS#11, Set Attribute, and Server to Client operations: Notify, Put, Discover Versions, QueryObjects Supported: Certificate, Certificate Request, Opaque Object, PGP Key, Private Key, Public Key, Secret Data, Split Key, Symmetric Key
KMIP 2.1 Operations Supported (both synchronous and asynchronous):
Create, Create Key Pair, Register, Re-key, Re-key Key Pair, Derive Key, Certify, Re-certify, Locate, Check, Get, Get Attributes, Get Attribute List, Add Attribute, Modify Attribute, Delete Attribute, Obtain Lease, Get Usage Allocation, Activate, Revoke, Destroy, Archive, Recover, Validate, Query (synch only), Discover Versions (synch only), Cancel, Poll, Encrypt (streaming/non-streaming), Decrypt (streaming/non-streaming), Sign (streaming/non-streaming), Signature Verify (streaming/non-streaming), MAC (streaming/non-streaming), MAC Verify (streaming/non-streaming), RNG Retrieve, RNG Seed, Hash (streaming/non-streaming), Create Split Key, Join Split Key, Export, Import, Adjust Attribute, Delegated Login, Interop, Log, Login, Logout, PKCS#11, Set Attribute, Get Constraints, Set Constraints, Set Defaults, Ping, Process, Query Asynchronous Requests, and Server to Client operations: Notify, Put, Discover Versions, QueryObjects Supported: Certificate, Certificate Request, Opaque Object, PGP Key, Private Key, Public Key, Secret Data, Split Key, Symmetric Key
KMIP 3.0 Operations Supported (both synchronous and asynchronous):
Activate, Add Attribute, Adjust Attribute, Archive, Cancel, Certify, Check, Create, Create Credential, Create Group, Create Key Pair, Create Split Key, Create User, Deactivate, Decrypt, Delegated Login, Delete Attribute, Derive Key, Destroy, Discover Versions, Encrypt, Export, Get, Get Attributes, Get Attribute List, Get Constraints, Get Usage Allocation, Hash, Import, Interop, Join Split Key, Locate, Log, Login, Logout, MAC, MAC Verify, Modify Attribute, Obiliterate, Obtain Lease, Ping, PKCS#11, Poll, Process, Query, Query Asynchronous Requests, Recover, Register, Revoke, Re-certify, Re-key, Re-key Key Pair, RNG Retrieve, RNG Seed, Set Attribute, Set Constraints, Set Defaults, Sign, Signature Verify, Validate, Encapsulate, DecapsulateObjects Supported:
System Objects: User, Group, Credentials
User Objects: Certificate, Certificate Request, Opaque Object, PGP Key, Private Key, Public Key, Secret Data, Split Key, Symmetric Key
Cryptographic Algorithms
- DES
- 3DES
- AES
- RSA
- DSA
- ECDSA
- HMAC-SHA1
- HMAC-SHA224
- HMAC-SHA256
- HMAC-SHA384
- HMAC-SHA512
- HMAC-MD5
- DH
- ECDH
- ECMQV
- Blowfish
- Camellia
- CAST5
- IDEA
- MARS
- RC2
- RC4
- RC5
- SKIPJACK
- Twofish
- EC
- OneTimePad
- ChaCha20
- Poly1305
- ChaCha20Poly1305
- SHA3-224
- SHA3-256
- SHA3-384
- SHA3-512
- HMAC-SHA3-224
- HMAC-SHA3-256
- HMAC-SHA3-384
- HMAC-SHA3-512
- SHAKE-128
- SHAKE-256
- ARIA
- SEED
- SM2
- SM3
- SM4
- GOST-R34.10_2012
- GOST-R34.11_2012
- GOST-R34.13_2015
- GOST-28147-89
- XMSS
- SPHINCS-256
- McEliece
- McEliece-6960119
- McEliece-8192128
- Ed25519
- Ed448
Supported Key Formats
- Raw
- Opaque
- PKCS#1
- PKCS#8
- PKCS#12
- X.509
- Transparent ECDSA Private Key
- Transparent ECDSA Public Key
- Transparent ECDH Private Key
- Transparent ECDH Public Key
- Transparent ECMQV Private Key
- Transparent ECMQV Public Key
- Transparent Symmetric Key
- Transparent DSA Public Key
- Transparent DSA Private Key
- Transparent RSA Public Key
- Transparent RSA Private Key
- Seed Private Key (For PQC keys)
Supported Platforms
SKC™ is currently supported on the following platforms:- Windows 10 (32bit/64bit), Windows Server 2016+ (32bit/64bit)
- Linux x86 Kernel 2.6+ (32bit/64bit)
- Linux ARM Kernel 2.6+ (32bit/64bit) (with source license)
- FreeBSD 14 x86 (64bit)
Included in the SKC Secure KMIP Client SDK, is our PKCS11 library
that meets the requirements for conformance of a PKCS #11 Extended Provider and Authentication
Token (see
PKCS11 Cryptographic Token Interface Profiles Version 2.40, 14-Apr-2015, OASIS Committee Specification 01 and
PKCS#11 Cryptographic Token Interface Profiles Version 3.0).
The library currently provides two tokens (The "KMIP" and "Keystore" tokens) and may be extended by customers
to provide their own token types via a plugin interface.
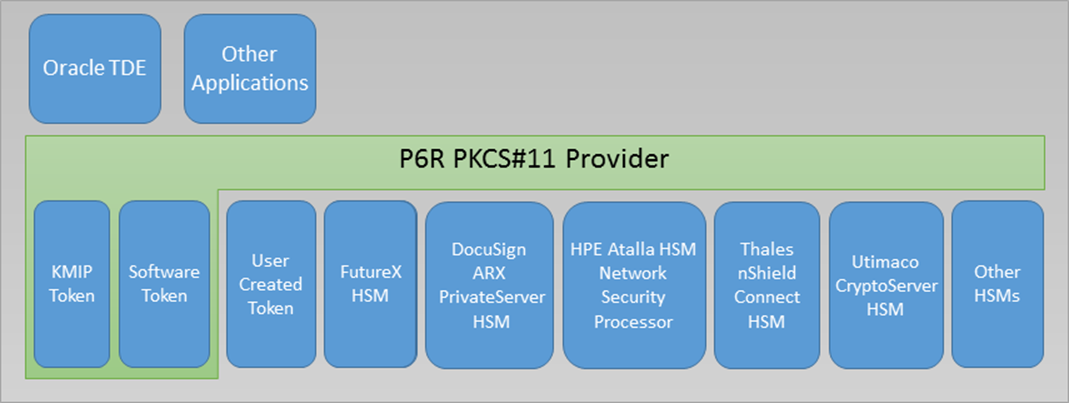
The KMIP Token
This token uses the facilities of a remote KMIP server to implement the features of the PKCS11 Version 2.40 and 3.0 APIs allowing developers familiar with PKCS11 to store their keys on a KMIP server without having to learn about the KMIP protocol or KMIP SDKs. Our PKCS11 library allows the definition of any number of KMIP tokens all pointing to the same or different KMIP servers.The Keystore Software Token
This token uses P6Rs cryptographic API and local secure Keystore to implement the features of the PKCS 11 Version 2.40 and 3.0 API. Our PKCS11 library allows the definition of any number of Keystore software tokens where each token gets its own separate secure Keystore to manage PKCS 11 objects.HSM Tokens
We have added tokens for these popular HSM's:- DocuSign ARX PrivateServer HSM
- FutureX HSM
- Utimaco Atalla HSM (Network Security Processor)
- nCipher/Thales nShield Connect HSM
- Utimaco CryptoServer HSM
- AWS CloudHSM
PKCS11 Functions Implemented By The KMIP Token
- C_Initialize
- C_Finalize
- C_GetInfo
- C_GetFunctionList
- C_GetSlotList
- C_GetSlotInfo
- C_GetTokenInfo
- C_GetMechanismList
- C_GetMechanismInfo
- C_InitToken
- C_InitPIN
- C_SetPIN
- C_OpenSession
- C_CloseSession
- C_CloseAllSessions
- C_GetSessionInfo
- C_Login
- C_Logout
- C_CreateObject
- C_DestroyObject
- C_GetAttributeValue
- C_SetAttributeValue
- C_FindObjectsInit
- C_FindObjects
- C_MessageEncryptInit
- C_MessageEncryptFinal
- C_EncryptMessage
- C_EncryptMessageBegin
- C_EncryptMessageNext
- C_MessageDecryptInit
- C_MessageDecryptFinal
- C_DecryptMessage
- C_DecryptMessageBegin
- C_DecryptMessageNext
- C_FindObjectsFinal
- C_GenerateKey (not including domain parameters)
- C_GenerateKeyPair
- C_SeedRandom
- C_GenerateRandom
- C_SignInit
- C_Sign
- C_VerifyInit
- C_Verify
- C_EncryptInit
- C_Encrypt
- C_EncryptUpdate
- C_EncryptFinal
- C_DecryptInit
- C_Decrypt
- C_DecryptUpdate
- C_DecryptFinal
- C_DigestInit
- C_Digest
- C_DigestUpdate
- C_DigestKey
- C_DigestFinal
- C_WrapKey
- C_UnwrapKey (if the KMIP server supports unwrapping)
- C_MessageSignInit
- C_MessageSignFinal
- C_SignMessage
- C_SignMessageBegin
- C_SignMessageNext
- C_MessageVerifyInit
- C_MessageVerifyFinal
- C_VerifyMessage
- C_VerifyMessageBegin
- C_VerifyMessageNext
PKCS11 Functions Implemented By The Keystore Token
- C_Initialize
- C_Finalize
- C_GetInfo
- C_GetFunctionList
- C_GetSlotList
- C_GetSlotInfo
- C_GetTokenInfo
- C_GetMechanismList
- C_GetMechanismInfo
- C_InitToken
- C_InitPIN
- C_SetPIN
- C_OpenSession
- C_FindObjectsFinal
- C_CloseSession
- C_CloseAllSessions
- C_GetSessionInfo
- C_Login
- C_Logout
- C_CreateObject
- C_DestroyObject
- C_GetAttributeValue
- C_SetAttributeValue
- C_FindObjectsInit
- C_FindObjects
- C_FindObjectsFinal
- C_GenerateKey (not including domain parameters)
- C_GenerateKeyPair
- C_GenerateRandom
- C_SignInit
- C_Sign
- C_VerifyInit
- C_Verify
- C_EncryptInit
- C_Encrypt
- C_EncryptUpdate
- C_EncryptFinal
- C_DecryptInit
- C_Decrypt
- C_DecryptUpdate
- C_DecryptFinal
- C_DigestInit
- C_Digest
- C_DigestUpdate
- C_DigestFinal
P6R is an OASIS contributing member of the
OASIS Key Management Interoperability Protocol (KMIP) Technical Commitee and of the OASIS PKCS 11 Technical Commitee.
The SKC KMIP Client SDK follows the standards defined in these documents.
The OASIS Key management Interoperability Protocol (KMIP) defines a single, comprehensive
protocol for communication between encryption systems and a broad range of new and
legacy enterprise applications, including email, databases, and storage devices.
Go to OASIS Key Management
Interoperability Protocol (KMIP) Technical Committee to learn more about the KMIP
standard.
OASIS PKCS #11 is a standard for cryptographic tokens controlling authentication information
(personal identity, cryptographic keys, certificates, digital signatures, biometric data).
Go to OASIS PKCS #11 Technical
Committee to learn more about the PKCS #11 standard.
Standards Reference Documents
P6R is an OASIS member and a contributing member of the
OASIS Key Management Interoperability Protocol (KMIP) Technical Commitee and of the OASIS PKCS 11 Technical Commitee.
The SKC™ Secure KMIP Client SDK conforms to the following standard defined test cases using Tag Type Length Value (TTLV), XML, and JSON message encodings for all tests.
- Supported KMIP Profiles
- KMIP Version 1.0 Test Cases Supported
- KMIP Version 1.0 Symmetric Key Lifecycle Profile
- KMIP Version 1.0 Symmetric Key Foundry for FIPS 140-2 Profile
- KMIP Version 1.0 Asymmetric Key Lifecycle Profile Supported
- KMIP Version 1.0 Opaque Managed Object Store Profile
- KMIP Version 1.0 KMIP Tape Library Profile Version 1.0
- KMIP Version 1.0 Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0
- SEPATON Profile Version 1.0
- KMIP Version 1.1 Test Cases Supported
- KMIP Version 1.1 - Symmetric Key Lifecycle Profile
- KMIP Version 1.1 - Symmetric Key Foundry for FIPS 140-2 Profile
- KMIP Version 1.1 - Asymmetric Key Lifecycle Profile Supported
- KMIP Version 1.1 - KMIP Opaque Managed Object Store Profile
- KMIP Version 1.1 - KMIP Tape Library Profile Version 1.0
- KMIP Version 1.1 - Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0
- KMIP Version 1.2 Test Cases Supported
- KMIP Version 1.2 - Symmetric Key Lifecycle Profile
- KMIP Version 1.2 - Symmetric Key Foundry for FIPS 140-2 Profile
- KMIP Version 1.2 - Asymmetric Key Lifecycle Profile Supported
- KMIP Version 1.2 - KMIP Opaque Managed Object Store Profile
- KMIP Version 1.2 - KMIP Tape Library Profile Version 1.0
- KMIP Version 1.2 - Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0
- KMIP Version 1.2 - KMIP Cryptographic Services Profile Supported
- KMIP 1.0, 1.1, 1.2 and 1.3 - KMIP Additional Message Encodings Supported
- KMIP 1.0, 1.1, 1.2 and 1.3 - KMIP Suite B Profile Version 1.0
- KMIP Version 1.3 Test Cases Supported
- KMIP Version 1.3 - Asymmetric Key Lifecycle Profile Supported
- KMIP Version 1.3 - KMIP Opaque Managed Object Store Profile
- KMIP Version 1.3 - KMIP Tape Library Profile Version 1.0
- KMIP Version 1.3 - Symmetric Key Foundry for FIPS 140-2 Profile
- KMIP Version 1.3 - Symmetric Key Lifecycle Profile
- KMIP Version 1.3 - Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0
- KMIP Version 1.3 - KMIP Cryptographic Services Profile Supported
- KMIP Version 1.4 - Test Cases Supported
- KMIP Version 2.0 - Test Cases Supported
- KMIP Version 2.1 - Test Cases Supported
- KMIP Version 3.0 - Test Cases Supported
- KMIP Version 3.0 - PQC Test Cases
Supported KMIP Profiles
| Profile |
|---|
| Baseline Client Basic KMIP V1.2 |
| Baseline Client TLS V1.2 KMIP V1.2 |
| Tape Library Client KMIP V1.0 |
| Tape Library Client KMIP V1.1 |
| Tape Library Client KMIP V1.2 |
| Symmetric Key Lifecycle Client KMIP V1.0 |
| Symmetric Key Lifecycle Client KMIP V1.1 |
| Symmetric Key Lifecycle Client KMIP V1.2 |
| Asymmetric Key Lifecycle Client KMIP V1.0 |
| Asymmetric Key Lifecycle Client KMIP V1.1 |
| Asymmetric Key Lifecycle Client KMIP V1.2 |
| Basic Cryptographic Client KMIP V1.2 |
| Advanced Cryptographic Client KMIP V1.2 |
| RNG Cryptographic Client KMIP V1.2 |
| Basic Symmetric Key Foundry Client KMIP V1.0 |
| Intermediate Symmetric Key Foundry Client KMIP V1.0 |
| Advanced Symmetric Key Foundry Client KMIP V1.0 |
| Basic Symmetric Key Foundry Client KMIP V1.1 |
| Intermediate Symmetric Key Foundry Client KMIP V1.1 |
| Advanced Symmetric Key Foundry Client KMIP V1.1 |
| Basic Symmetric Key Foundry Client KMIP V1.2 |
| Intermediate Symmetric Key Foundry Client KMIP V1.2 |
| Advanced Symmetric Key Foundry Client KMIP V1.2 |
| Opaque Managed Object Store Client KMIP V1.0 |
| Opaque Managed Object Store Client KMIP V1.1 |
| Opaque Managed Object Store Client KMIP V1.2 |
| Suite B MinLOS 128 Client KMIP V1.0 |
| Suite B MinLOS 128 Client KMIP V1.1 |
| Suite B MinLOS 128 Client KMIP V1.2 |
| Suite B MinLOS 192 Client KMIP V1.0 |
| Suite B MinLOS 192 Client KMIP V1.1 |
| Suite B MinLOS 192 Client KMIP V1.2 |
| Storage Array With Self Encrypting Drive Client KMIP V1.0 |
| Storage Array With Self Encrypting Drive Client KMIP V1.1 |
| Storage Array With Self Encrypting Drive Client KMIP V1.2 |
| HTTPS Client KMIP V1.0 |
| HTTPS Client KMIP V1.1 |
| HTTPS Client KMIP V1.2 |
| JSON Client KMIP V1.0 |
| JSON Client KMIP V1.1 |
| JSON Client KMIP V1.2 |
| XML Client KMIP V1.0 |
| XML Client KMIP V1.1 |
| XML Client KMIP V1.2 |
| Baseline Client Basic KMIP V1.3 |
| Baseline Client TLS V1.2 KMIP V1.3 |
| Tape Library Client KMIP V1.3 |
| Symmetric Key Lifecycle Client KMIP V1.3 |
| Asymmetric Key Lifecycle Client KMIP V1.3 |
| Basic Cryptographic Client KMIP V1.3 |
| Advanced Cryptographic Client KMIP V1.3 |
| RNG Cryptographic Client KMIP V1.3 |
| Basic Symmetric Key Foundry Client KMIP V1.3 |
| Intermediate Symmetric Key Foundry Client KMIP V1.3 |
| Advanced Symmetric Key Foundry Client KMIP V1.3 |
| Opaque Managed Object Store Client KMIP V1.3 |
| Suite B minLOS 128 Client KMIP V1.3 |
| Suite B minLOS 192 Client KMIP V1.3 |
| Storage Array With Self Encrypting Drive Client KMIP V1.3 |
| HTTPS Client KMIP V1.3 |
| JSON Client KMIPV 1.3 |
| XML Client KMIP V1.3 |
| Baseline Client Basic KMIP V1.4 |
| Baseline Client TLS V1.2 KMIP V1.4 |
| Tape Library Client KMIP V1.4 |
| Symmetric Key Lifecycle Client KMIP V1.4 |
| Asymmetric Key Lifecycle Client KMIP V1.4 |
| Basic Cryptographic Client KMIP V1.4 |
| Advanced Cryptographic Client KMIP V1.4 |
| RNG Cryptographic Client KMIP V1.4 |
| Basic Symmetric Key Foundry Client KMIP V1.4 |
| Intermediate Symmetric Key Foundry Client KMIP V1.4 |
| Advanced Symmetric Key Foundry Client KMIP V1.4 |
| Opaque Managed Object Store Client KMIP V1.4 |
| Suite B minLOS 128 Client KMIP V1.4 |
| Suite B minLOS 192 Client KMIP V1.4 |
| Storage Array With Self Encrypting Drive Client KMIP V1.4 |
| HTTPS Client KMIP V1.4 |
| JSON Client KMIP V1.4 |
| XML Client KMIP V1.4 |
KMIP Version 1.0 Test Cases Supported
| Test Case | Description |
|---|---|
| TC-311-10 | Create / Destroy |
| TC-312-10 | Register / Create / Get attributes / Destroy |
| TC-313-10 | Create / Locate / Get / Destroy |
| TC-314-10 | Dual Client Test Case, ID Placeholder-linked Locate & Get Batch |
| TC-315-10 | Register / Destroy Secret Data |
| TC-32-10 | Asynchronous Locate |
| TC-41-10 | Revoke Scenario |
| TC-51-10 | Get Usage Allocation Scenario |
| TC-61-10 | Import of a Third-party Key |
| TC-71-10 | Unrecognized Message Extension with Criticality Indicator False |
| TC-72-10 | Unrecognized Message Extension with Criticality Indicator True |
| TC-81-10 | Create a Key Pair |
| TC-82-10 | Register Both Halves of a Key Pair |
| TC-91-10 | Create a Key, Re-key |
| TC-92-10 | Existing Key Expired, Re-key with Same Life-cycle |
| TC-93-10 | Existing Key Compromised, Re-key with Same Life-cycle |
| TC-94-10 | Create Key, Re-key with New Life-cycle |
| TC-95-10 | Obtain Lease for Expired Key |
| TC-101-10 | Create a Key, Archive and Recover it |
| TC-111-10 | Credential, Operation Policy, Destroy Date |
| TC-121-10 | Query, Maximum Response Size |
| TC-131-10 | Register an Asymmetric Key Pair in PKCS1 Format |
| TC-132-10 | Register an Asymmetric Key Pair and a Corresponding X509 Certificate |
| TC-134-10 | Register Key Pair, Certify and Re-certify Public Key |
| TC-NP-1-10 | Put |
| TC-NP-2-10 | Notify & Put |
| TC-ECC-1-10 | Register an ECC Key Pai |
| TC-ECC-2-10 | Register an ECC Key Pair in PKCS8 Format |
| TC-ECC-3-10 | Register an ECC Key Pair and ECDSA Certificate |
| TC-DERIVEKEY-1-10 | Derive Symmetric Key HASH |
| TC-DERIVEKEY-2-10 | Derive Symmetric Key HMAC |
| TC-DERIVEKEY-3-10 | Derive Symmetric Key with secret data |
| TC-DERIVEKEY-4-10 | Derive Symmetric Key with secret data |
| TC-DERIVEKEY-5-10 | Derive Symmetric Key with secret data |
| TC-REKEY-1-10 | Rekey multiple times |
| TC-AESXTS-1-10 | Two key encryption |
| TC-I18N-1-10 | Unicode characters in attributes values |
| TC-I18N-2-10 | Unicode characters in attributes values |
| TC-I18N-3-10 | Unicode characters in attributes values and custom attribute names |
| TC-AESXTS-1-10 | Two key encryption |
| TC-I18N-1-10 | UTF8 character in attribute |
| TC-I18N-2-10 | UTF8 character in attribute |
| TC-I18N-3-10 | UTF8 character in attribute |
| TC-REKEY-1-10 | Rekey multiple times |
| TC-DERIVEKEY-1-10 | Derive Symmetric Key |
| TC-DERIVEKEY-2-10 | Derive Symmetric Key |
| TC-DERIVEKEY-3-10 | Derive Symmetric Key |
| TC-DERIVEKEY-4-10 | Derive Symmetric Key |
| TC-DERIVEKEY-5-10 | Derive Symmetric Key |
KMIP Version 1.0 Symmetric Key Lifecycle Profile
| Test Case | Description |
|---|---|
| SKLC-M-1-10 | Create, GetAttributes, Destroy |
| SKLC-M-2-10 | Create, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| SKLC-M-3-10 | Create, GetAttributes, Activate, GetAttributes, ModifyAttribute, Revoke, GetAttributes, Destroy |
| SKLC-O-1-10 | Create, GetAttributes, Destroy, GetAttributes |
KMIP Version 1.0 Symmetric Key Foundry for FIPS 140-2 Profile
| Test Case | Description |
|---|---|
| SKFF-M-1-10 | Create, Destroy AES-128 |
| SKFF-M-2-10 | Create, Destroy AES-192 |
| SKFF-M-3-10 | Create, Destroy AES-256 |
| SKFF-M-4-10 | Create, Destroy DES3-168 |
| SKFF-M-5-10 | Create, Locate, Get, Destroy, Locate AES-128 |
| SKFF-M-6-10 | Create, Locate, Get, Destroy, Locate AES-192 |
| SKFF-M-7-10 | Create, Locate, Get, Destroy, Locate AES-256 |
| SKFF-M-8-10 | Create, Locate, Get, Destroy, Locate DES3-168 |
| SKFF-M-9-10 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-128 |
| SKFF-M-10-10 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-192 |
| SKFF-M-11-10 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-256 |
| SKFF-M-12-10 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-168 |
| SKFF-O-1-10 | Create, Destroy SKIPJACK-80 |
| SKFF-O-2-10 | Create, Locate, Get, Destroy, Locate SKIPJACK-80 |
| SKFF-O-3-10 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy SKIPJACK-80 |
| SKFF-O-4-10 | Create, Destroy DES3-112 |
| SKFF-O-5-10 | Create, Locate, Get, Destroy, Locate DES3-112 |
| SKFF-O-6-10 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-112 |
KMIP Version 1.0 Asymmetric Key Lifecycle Profile Supported
| Test Case | Description |
|---|---|
| AKLC-M-1-10 | CreateKeyPair, GetAttributes, GetAttributes, Destroy |
| AKLC-M-2-10 | CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| AKLC-M-3-10 | CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| AKLC-O-1-10 | CreateKeyPair, GetAttributes, Destroy, GetAttributes |
KMIP Version 1.0 Opaque Managed Object Store Profile
| Test Case | Description |
|---|---|
| OMOS-M-1-10 | Register small opaque objecty |
| OMOS-O-1-10 | Register large (>10k) opaque objecty |
KMIP Version 1.0 KMIP Tape Library Profile Version 1.0
| Test Case | Description |
|---|---|
| TL-M-1-10 | Configuration |
| TL-M-2-10 | Write with new (created) key |
| TL-M-3-10 | Read an encrypted tape |
KMIP Version 1.0 Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0
| Test Case | Description |
|---|---|
| SASED-M-1-10 | Configuration |
| SASED-M-2-10 | Register the authentication key |
| SASED-M-3-10 | Retrieve Authentication Key |
SEPATON Profile Version 1.0
| Test Case | Description |
|---|---|
| SEPATON-1-10 | Query |
| SEPATON-2-10 | Locate, Create |
| SEPATON-3-10 | Locate, Get, GetAttributes, Activate, GetAttributes |
KMIP Version 1.1 Test Cases Supported
| Test Case | Description |
|---|---|
| TC-311-11 | Create / Destroy |
| TC-312-11 | Register / Create / Get attributes / Destroy |
| TC-313-11 | Create / Locate / Get / Destroy |
| TC-314-11 | Dual Client Test Case, ID Placeholder-linked Locate & Get Batch |
| TC-315-11 | Register / Destroy Secret Data |
| TC-32-11 | Asynchronous Locate |
| TC-41-11 | Revoke Scenario |
| TC-51-11 | Get Usage Allocation Scenario |
| TC-61-11 | Import of a Third-party Key |
| TC-71-11 | Unrecognized Message Extension with Criticality Indicator False |
| TC-72-11 | Unrecognized Message Extension with Criticality Indicator True |
| TC-81-11 | Create a Key Pair |
| TC-82-11 | Register Both Halves of a Key Pair |
| TC-91-11 | Create a Key, Re-key |
| TC-92-11 | Existing Key Expired, Re-key with Same Life-cycle |
| TC-93-11 | Existing Key Compromised, Re-key with Same Life-cycle |
| TC-94-11 | Create Key, Re-key with New Life-cycle |
| TC-95-11 | Obtain Lease for Expired Key |
| TC-101-11 | Create a Key, Archive and Recover it |
| TC-111-11 | Credential, Operation Policy, Destroy Date |
| TC-112-11 | Device Credential, Operation Policy, Destroy Date |
| TC-121-11 | Query, Maximum Response Size |
| TC-122-11 | Query Vendor Extensions |
| TC-131-11 | Register an Asymmetric Key Pair in PKCS1 Format |
| TC-132-11 | Register an Asymmetric Key Pair and a Corresponding X509 Certificate |
| TC-133-11 | Create, Re-key Key Pair |
| TC-134-11 | Register Key Pair, Certify and Re-certify Public Key |
| TC-141-11 | Key Wrapping using AES Key Wrap and No Encoding |
| TC-142-11 | Key Wrapping using AES Key Wrap with Attributes |
| TC-151-11 | Locate a Fresh Object from the Default Group |
| TC-152-11 | Client-side Group Management |
| TC-153-11 | Default Object Group Member |
| TC-161-11 | Discover Versions |
| TC-171-11 | Handling of Attributes and Attribute Index Values |
| TC-181-11 | Digests of Symmetric Keys |
| TC-182-11 | Digests of RSA Private Keys |
| TC-NP-1-11 | Put |
| TC-NP-2-11 | Notify & Put |
| TC-ECC-1-11 | Register an ECC Key Pair |
| TC-ECC-2-11 | Register an ECC Key Pair in PKCS8 Format |
| TC-ECC-3-11 | Register an ECC Key Pair and ECDSA Certificate |
| TC-DERIVEKEY-1-11 | Derive Symmetric Key HASH |
| TC-DERIVEKEY-2-11 | Derive Symmetric Key HMAC |
| TC-DERIVEKEY-3-11 | Derive Symmetric Key with secret data |
| TC-DERIVEKEY-4-11 | Derive Symmetric Key with secret data |
| TC-DERIVEKEY-5-11 | Derive Symmetric Key with secret data |
| TC-REKEY-1-11 | Rekey multiple times |
| TC-AESXTS-1-11 | Two key encryption |
| TC-I18N-1-11 | Unicode characters in attributes values |
| TC-I18N-2-11 | Unicode characters in attributes values |
| TC-I18N-3-11 | Unicode characters in attributes values and custom attribute names |
| TC-AESXTS-1-11 | Two key encryption |
| TC-I18N-1-11 | UTF8 character in attribute |
| TC-I18N-2-11 | UTF8 character in attribute |
| TC-I18N-3-11 | UTF8 character in attribute |
| TC-REKEY-1-11 | Rekey multiple times |
| TC-DERIVEKEY-1-11 | Derive Symmetric Key |
| TC-DERIVEKEY-2-11 | Derive Symmetric Key |
| TC-DERIVEKEY-3-11 | Derive Symmetric Key |
| TC-DERIVEKEY-4-11 | Derive Symmetric Key |
| TC-DERIVEKEY-5-11 | Derive Symmetric Key |
KMIP Version 1.1 - Symmetric Key Lifecycle Profile
| Test Case | Description |
|---|---|
| SKLC-M-1-11 | Create, GetAttributes, Destroy |
| SKLC-M-2-11 | Create, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| SKLC-M-3-11 | Create, GetAttributes, Activate, GetAttributes, ModifyAttribute, Revoke, GetAttributes, Destroy |
| SKLC-O-1-11 | Create, GetAttributes, Destroy, GetAttributes |
KMIP Version 1.1 - Symmetric Key Foundry for FIPS 140-2 Profile
| Test Case | Description |
|---|---|
| SKFF-M-1-11 | Create, Destroy AES-128 |
| SKFF-M-2-11 | Create, Destroy AES-192 |
| SKFF-M-3-11 | Create, Destroy AES-256 |
| SKFF-M-4-11 | Create, Destroy DES3-168 |
| SKFF-M-5-11 | Create, Locate, Get, Destroy, Locate AES-128 |
| SKFF-M-6-11 | Create, Locate, Get, Destroy, Locate AES-192 |
| SKFF-M-7-11 | Create, Locate, Get, Destroy, Locate AES-256 |
| SKFF-M-8-11 | Create, Locate, Get, Destroy, Locate DES3-168 |
| SKFF-M-9-11 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-128 |
| SKFF-M-10-11 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-192 |
| SKFF-M-11-11 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-256 |
| SKFF-M-12-11 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-168 |
| SKFF-O-1-11 | Create, Destroy SKIPJACK-80 |
| SKFF-O-2-11 | Create, Locate, Get, Destroy, Locate SKIPJACK-80 |
| SKFF-O-3-11 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy SKIPJACK-80 |
| SKFF-O-4-11 | Create, Destroy DES3-112 |
| SKFF-O-5-11 | Create, Locate, Get, Destroy, Locate DES3-112 |
| SKFF-O-6-11 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-112 |
KMIP Version 1.1 - Asymmetric Key Lifecycle Profile Supported
| Test Case | Description |
|---|---|
| AKLC-M-1-11 | CreateKeyPair, GetAttributes, GetAttributes, Destroy |
| AKLC-M-2-11 | CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| AKLC-M-3-11 | CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| AKLC-O-1-11 | CreateKeyPair, GetAttributes, Destroy, GetAttributes |
KMIP Version 1.1 - KMIP Opaque Managed Object Store Profile
| Test Case | Description |
|---|---|
| OMOS-M-1-11 | Register small opaque object |
| OMOS-O-1-11 | Register large (>10k) opaque object |
KMIP Version 1.1 - KMIP Tape Library Profile Version 1.0
| Test Case | Description |
|---|---|
| TL-M-1-11 | Configuration |
| TL-M-2-11 | Write with new (created) key |
| TL-M-3-11 | Read an encrypted tape |
KMIP Version 1.1 - Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0
| Test Case | Description |
|---|---|
| SASED-M-1-11 | Configuration |
| SASED-M-2-11 | Register the authentication key |
| SASED-M-3-11 | Retrieve Authentication Key |
KMIP Version 1.2 Test Cases Supported
| Test Case | Description |
|---|---|
| TC-311-12 | Create / Destroy |
| TC-312-12 | Register / Create / Get attributes / Destroy |
| TC-313-12 | Create / Locate / Get / Destroy |
| TC-314-12 | Dual Client Test Case, ID Placeholder-linked Locate & Get Batch |
| TC-315-12 | Register / Destroy Secret Data |
| TC-32-12 | Asynchronous Locate |
| TC-41-12 | Revoke Scenario |
| TC-51-12 | Get Usage Allocation Scenario |
| TC-61-12 | Import of a Third-party Key |
| TC-71-12 | Unrecognized Message Extension with Criticality Indicator False |
| TC-72-12 | Unrecognized Message Extension with Criticality Indicator True |
| TC-81-12 | Create a Key Pair |
| TC-82-12 | Register Both Halves of a Key Pair |
| TC-91-12 | Create a Key, Re-key |
| TC-92-12 | Existing Key Expired, Re-key with Same Life-cycle |
| TC-93-12 | Existing Key Compromised, Re-key with Same Life-cycle |
| TC-94-12 | Create Key, Re-key with New Life-cycle |
| TC-95-12 | Obtain Lease for Expired Key |
| TC-101-12 | Create a Key, Archive and Recover it |
| TC-111-12 | Credential, Operation Policy, Destroy Date |
| TC-112-12 | Device Credential, Operation Policy, Destroy Date |
| TC-121-12 | Query, Maximum Response Size |
| TC-122-12 | Query Vendor Extensions |
| TC-131-12 | Register an Asymmetric Key Pair in PKCS1 Format |
| TC-132-12 | Register an Asymmetric Key Pair and a Corresponding X509 Certificate |
| TC-133-12 | Create, Re-key Key Pair |
| TC-134-12 | Register Key Pair, Certify and Re-certify Public Key |
| TC-141-12 | Key Wrapping using AES Key Wrap and No Encoding |
| TC-142-12 | Key Wrapping using AES Key Wrap with Attributes |
| TC-151-12 | Locate a Fresh Object from the Default Group |
| TC-152-12 | Client-side Group Management |
| TC-153-12 | Default Object Group Member |
| TC-161-12 | Discover Versions |
| TC-171-12 | Handling of Attributes and Attribute Index Values |
| TC-181-12 | Digests of Symmetric Keys |
| TC-182-12 | Digests of RSA Private Keys |
| TC-PGP-1-12 | Register PGP Key - RSA |
| TC-MDO-1-12 | Register MDO Key |
| TC-MDO-2-12 | Locate MDO keys by Key Value Present |
| TC-MDO-3-12 | Register MDO Key using PKCS11 URI |
| TC-SJ-1-12 | Create and Split/Join |
| TC-SJ-2-12 | Register and Split / Join |
| TC-SJ-3-12 | Join Split Keys |
| TC-SJ-4-12 | Register and Split / Join with XOR |
| TC-NP-1-12 | Put |
| TC-NP-2-12 | Notify & Put |
| TC-ECC-1-12 | Register an ECC Key Pair |
| TC-ECC-2-12 | Register an ECC Key Pair in PKCS8 Format |
| TC-ECC-3-12 | Register an ECC Key Pair and ECDSA Certificate |
| TC-DERIVEKEY-1-12 | Derive Symmetric Key HASH |
| TC-DERIVEKEY-2-12 | Derive Symmetric Key HMAC |
| TC-DERIVEKEY-3-12 | Derive Symmetric Key with secret data |
| TC-DERIVEKEY-4-12 | Derive Symmetric Key with secret data |
| TC-DERIVEKEY-5-12 | Derive Symmetric Key with secret data |
| TC-REKEY-1-12 | Rekey multiple times |
| TC-AESXTS-1-12 | Two key encryption |
| TC-I18N-1-12 | Unicode characters in attributes values |
| TC-I18N-2-12 | Unicode characters in attributes values |
| TC-I18N-3-12 | Unicode characters in attributes values and custom attribute names |
| TC-AESXTS-1-12 | Two key encryption |
| TC-I18N-1-12 | UTF8 character in attribute |
| TC-I18N-2-12 | UTF8 character in attribute |
| TC-I18N-3-12 | UTF8 character in attribute |
| TC-REKEY-1-12 | Rekey multiple times |
| TC-DERIVEKEY-1-12 | Derive Symmetric Key |
| TC-DERIVEKEY-2-12 | Derive Symmetric Key |
| TC-DERIVEKEY-3-12 | Derive Symmetric Key |
| TC-DERIVEKEY-4-12 | Derive Symmetric Key |
| TC-DERIVEKEY-5-12 | Derive Symmetric Key |
KMIP Version 1.2 - Symmetric Key Lifecycle Profile
| Test Case | Description |
|---|---|
| SKLC-M-1-12 | Create, GetAttributes, Destroy |
| SKLC-M-2-12 | Create, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| SKLC-M-3-12 | Create, GetAttributes, Activate, GetAttributes, ModifyAttribute, Revoke, GetAttributes, Destroy |
| SKLC-O-1-12 | Create, GetAttributes, Destroy, GetAttributes |
KMIP Version 1.2 - Symmetric Key Foundry for FIPS 140-2 Profile
| Test Case | Description |
|---|---|
| SKFF-M-1-12 | Create, Destroy AES-128 |
| SKFF-M-2-12 | Create, Destroy AES-192 |
| SKFF-M-3-12 | Create, Destroy AES-256 |
| SKFF-M-4-12 | Create, Destroy DES3-168 |
| SKFF-M-5-12 | Create, Locate, Get, Destroy, Locate AES-128 |
| SKFF-M-6-12 | Create, Locate, Get, Destroy, Locate AES-192 |
| SKFF-M-7-12 | Create, Locate, Get, Destroy, Locate AES-256 |
| SKFF-M-8-12 | Create, Locate, Get, Destroy, Locate DES3-168 |
| SKFF-M-9-12 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-128 |
| SKFF-M-10-12 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-192 |
| SKFF-M-11-12 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-256 |
| SKFF-M-12-12 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-168 |
| SKFF-O-1-12 | Create, Destroy SKIPJACK-80 |
| SKFF-O-2-12 | Create, Locate, Get, Destroy, Locate SKIPJACK-80 |
| SKFF-O-3-12 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy SKIPJACK-80 |
| SKFF-O-4-12 | Create, Destroy DES3-112 |
| SKFF-O-5-12 | Create, Locate, Get, Destroy, Locate DES3-112 |
| SKFF-O-6-12 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-112 |
KMIP Version 1.2 - Asymmetric Key Lifecycle Profile Supported
| Test Case | Description |
|---|---|
| AKLC-M-1-12 | CreateKeyPair, GetAttributes, GetAttributes, Destroy |
| AKLC-M-2-12 | CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| AKLC-M-3-12 | CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| AKLC-O-1-12 | CreateKeyPair, GetAttributes, Destroy, GetAttributes |
KMIP Version 1.2 - KMIP Opaque Managed Object Store Profile
| Test Case | Description |
|---|---|
| OMOS-M-1-12 | Register small opaque object |
| OMOS-O-1-12 | Register large (>10k) opaque object |
KMIP Version 1.2 - KMIP Tape Library Profile Version 1.0
| Test Case | Description |
|---|---|
| TL-M-1-12 | Configuration |
| TL-M-2-12 | Write with new (created) key |
| TL-M-3-12 | Read an encrypted tape |
KMIP Version 1.2 - Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0
| Test Case | Description |
|---|---|
| SASED-M-1-12 | Configuration |
| SASED-M-2-12 | Register the authentication key |
| SASED-M-3-12 | Retrieve Authentication Key |
KMIP Version 1.2 - KMIP Cryptographic Services Profile Supported
| Test Case | Description |
|---|---|
| CS-BC-M-1-12 | Encrypt with New Symmetric Key |
| CS-BC-M-2-12 | Decrypt with New Symmetric Key |
| CS-BC-M-3-12 | Encrypt and Decrypt with New Symmetric Key |
| CS-BC-M-4-12 | Encrypt with Known Symmetric Key |
| CS-BC-M-5-12 | Decrypt with Known Symmetric Key |
| CS-BC-M-6-12 | Encrypt and Decrypt with Known Symmetric Key |
| CS-BC-M-7-12 | Encrypt with Known Symmetric Key with Usage Limits |
| CS-BC-M-8-12 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding |
| CS-BC-M-9-12 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding |
| CS-BC-M-10-12 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC |
| CS-BC-M-11-12 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC and IV |
| CS-BC-M-12-12 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC and IV |
| CS-BC-M-13-12 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC and Random IV |
| CS-BC-M-14-12 | Encrypt and Decrypt with Known Symmetric Key Date Checks |
| CS-RNG-M-1-12 | RNG Retrieve |
| CS-RNG-O-1-12 | Seed RNG with Server Accept |
| CS-RNG-O-2-12 | Seed RNG with Server Partial Acceptt |
| CS-RNG-O-3-12 | Seed RNG with Server Ignoret |
| CS-RNG-O-4-12 | Seed RNG with Server Denyt |
| CS-AC-M-1-12 | Sign with Known Asymmetric Key |
| CS_AC-M-2-12 | Signature Verify with Known Asymmetric Key |
| CS-AC-M-3-12 | Sign and Signature Verify with Known Asymmetric Key |
| CS-AC-M-4-12 | MAC with Known Key |
| CS_AC-M-5-12 | MAC Verify with Known Key |
| CS-AC-M-6-12 | MAC and MAC Verify with Known Key |
| CS-AC-M-7-12 | Hash |
| CS-AC-M-8-12 | Sign and Signature Verify with Known Asymmetric Key Date Checks |
KMIP 1.0, 1.1, 1.2 and 1.3 - KMIP Additional Message Encodings Supported
| Test Case | Description |
|---|---|
| MSGENC-HTTPS-1-10 | HTTPS POST: Query, Maximum Response Size |
| MSGENC-XML-1-10 | Message Encoding XML: Query, Maximum Response Size (In addition, we have run all above test cases in XML mode.) |
| MSGENC-JSON-1-10 | Message Encoding JSON: Query, Maximum Response Size (In addition, we have run all above test cases in JSON mode.) |
KMIP 1.0, 1.1, 1.2, and 1.3 - KMIP Suite B Profile Version 1.0
| Test Case | Description |
|---|---|
| SUITEB_128-M-1-10 Query | |
| SUITEB_192-M-1-10 Query | |
| SUITEB_128-M-1-11 Query | |
| SUITEB_192-M-1-11 Query | |
| SUITEB_128-M-1-12 Query | |
| SUITEB_192-M-1-12 Query |
KMIP Version 1.3 Test Cases Supported
| Test Case | Description |
|---|---|
| TC-CREG-2-13 | Retrieve Initial Client Credentials |
| TC-OTP-1-13 | One Time Pad support |
| TC-OTP-2-13 | One Time Pad support |
| TC-OTP-3-13 | One Time Pad support |
| TC-OTP-4-13 | One Time Pad support |
| TC-Q-CAP-1-13 | Query Server Capabilities |
| TC-Q-CAP-2-13 | Query Server Capabilities |
| TC-Q-CREG_1-13 | Query Server Client Registration Methods |
| TC-Q-PROF-1-13 | Query Server supported profiles |
| TC-Q-PROF-2-13 | Query Server supported profiles |
| TC-Q-PROF-3-13 | Query Server supported profiles |
| TC-Q-RNGS-1-13 | Query Server supported RNG |
| TC-Q-RNGS-2-13 | Query Server supported RNG |
| TC-Q-RNGS-3-13 | Query Server supported RNG |
| TC-Q-RNGS-4-13 | Query Server supported RNG |
| TC-Q-RNGS-5-13 | Query Server supported RNG |
| TC-Q-S2C-1-13 | Server to Client Query client capabilities |
| TC-Q-S2C-2-13 | Server to Client Query client supported KMIP protocol versions |
| TC-Q-S2C-PROF-1-13 | Server to Client Query client supported profiles |
| TC-Q-S2C-PROF-2-13 | Server to Client Query client supported profiles |
| TC-Q-VAL-1-13 | Query Server Validations |
| TC-Q-VAL-2-13 | Query Server Validations |
| TC-RNG-ATTR-1-13 | Register / Get Attributes / Destroy |
| TC-RNG-ATTR-2-13 | Register / Get Attributes / Destroy |
| TC-STREAM-HASH-1-13 | Streaming) Hash |
| TC-STREAM-HASH-2-13 | Streaming) Hash |
| TC-STREAM-HASH-3-13 | Streaming) Hash |
| TC-STREAM-ENC-1-13 | Streaming) Encrypt with New Symmetric Key |
| TC-STREAM-ENC-2-13 | Streaming) Encrypt with Known Symmetric Key |
| TC-STREAM-ENCDEC-1-13 | Streaming) Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC |
| TC-OFFSET-1-13 | Locate with offset |
| TC-OFFSET-2-13 | Locate with offset |
| TC-DERIVEKEY-1-13 | Derive Symmetric Key HASH |
| TC-DERIVEKEY-2-13 | Derive Symmetric Key HMAC |
| TC-DERIVEKEY-3-13 | Derive Symmetric Key with secret data |
| TC-DERIVEKEY-4-13 | Derive Symmetric Key with secret data |
| TC-DERIVEKEY-5-13 | Derive Symmetric Key with secret data |
| TC-REKEY-1-13 | Rekey multiple times |
| TC-AESXTS-1-13 | Two key encryption |
| TC-I18N-1-13 | Unicode characters in attributes values |
| TC-I18N-2-13 | Unicode characters in attributes values |
| TC-I18N-3-13 | Unicode characters in attributes values and custom attribute names |
| TC-AESXTS-1-13 | Two key encryption |
| TC-OTP-5-13 | One Time Pad support |
| TC-I18N-1-13 | UTF8 character in attribute |
| TC-I18N-2-13 | UTF8 character in attribute |
| TC-I18N-3-13 | UTF8 character in attribute |
| TC-REKEY-1-13 | Rekey multiple times |
| TC-DERIVEKEY-1-13 | Derive Symmetric Key |
| TC-DERIVEKEY-2-13 | Derive Symmetric Key |
| TC-DERIVEKEY-3-13 | Derive Symmetric Key |
| TC-DERIVEKEY-4-13 | Derive Symmetric Key |
| TC-DERIVEKEY-5-13 | Derive Symmetric Key |
KMIP Version 1.3 - Asymmetric Key Lifecycle Profile Supported
| Test Case | Description |
|---|---|
| AKLC-M-1-13 | CreateKeyPair, GetAttributes, GetAttributes, Destroy |
| AKLC-M-2-13 | CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| AKLC-M-3-13 | CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| AKLC-O-1-13 | CreateKeyPair, GetAttributes, Destroy, GetAttributes |
KMIP Version 1.3 - KMIP Opaque Managed Object Store Profile
| Test Case | Description |
|---|---|
| OMOS-M-1-13 | Register small opaque object |
| OMOS-O-1-13 | Register large (>10k) opaque object |
KMIP Version 1.3 - KMIP Tape Library Profile Version 1.0
| Test Case | Description |
|---|---|
| TL-M-1-13 | Configuration |
| TL-M-2-13 | Write with new (created) key |
| TL-M-3-13 | Read an encrypted tape |
KMIP Version 1.3 - Symmetric Key Foundry for FIPS 140-2 Profile
| Test Case | Description |
|---|---|
| SKFF-M-1-13 | Create, Destroy AES-128 |
| SKFF-M-2-13 | Create, Destroy AES-192 |
| SKFF-M-3-13 | Create, Destroy AES-256 |
| SKFF-M-4-13 | Create, Destroy DES3-168 |
| SKFF-M-5-13 | Create, Locate, Get, Destroy, Locate AES-128 |
| SKFF-M-6-13 | Create, Locate, Get, Destroy, Locate AES-192 |
| SKFF-M-7-13 | Create, Locate, Get, Destroy, Locate AES-256 |
| SKFF-M-8-13 | Create, Locate, Get, Destroy, Locate DES3-168 |
| SKFF-M-9-13 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-128 |
| SKFF-M-10-13 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-192 |
| SKFF-M-11-13 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-256 |
| SKFF-M-12-13 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-168 |
| SKFF-O-1-13 | Create, Destroy SKIPJACK-80 |
| SKFF-O-2-13 | Create, Locate, Get, Destroy, Locate SKIPJACK-80 |
| SKFF-O-3-13 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy SKIPJACK-80 |
| SKFF-O-4-13 | Create, Destroy DES3-112 |
| SKFF-O-5-13 | Create, Locate, Get, Destroy, Locate DES3-112 |
| SKFF-O-6-13 | Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-112 |
KMIP Version 1.3 - Symmetric Key Lifecycle Profile
| Test Case | Description |
|---|---|
| SKLC-M-1-13 | Create, GetAttributes, Destroy |
| SKLC-M-2-13 | Create, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy |
| SKLC-M-3-13 | Create, GetAttributes, Activate, GetAttributes, ModifyAttribute, Revoke, GetAttributes, Destroy |
| SKLC-O-1-13 | Create, GetAttributes, Destroy, GetAttributes |
KMIP Version 1.3 - Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0
| Test Case | Description |
|---|---|
| SASED-M-1-13 | Configuration |
| SASED-M-2-13 | Register the authentication key |
| SASED-M-3-13 | Retrieve Authentication Key |
KMIP Version 1.3 - KMIP Cryptographic Services Profile Supported
| Test Case | Description |
|---|---|
| CS-BC-M-1-13 | Encrypt with New Symmetric Key |
| CS-BC-M-2-13 | Decrypt with New Symmetric Key |
| CS-BC-M-3-13 | Encrypt and Decrypt with New Symmetric Key |
| CS-BC-M-4-13 | Encrypt with Known Symmetric Key |
| CS-BC-M-5-13 | Decrypt with Known Symmetric Key |
| CS-BC-M-6-13 | Encrypt and Decrypt with Known Symmetric Key |
| CS-BC-M-7-13 | Encrypt with Known Symmetric Key with Usage Limits |
| CS-BC-M-8-13 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding |
| CS-BC-M-9-13 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding |
| CS-BC-M-10-13 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC |
| CS-BC-M-11-13 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC and IV |
| CS-BC-M-12-13 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC and IV |
| CS-BC-M-13-13 | Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC and Random IV |
| CS-BC-M-14-13 | Encrypt and Decrypt with Known Symmetric Key Date Checks |
| CS-RNG-M-1-13 | RNG Retrieve |
| CS-RNG-O-1-13 | Seed RNG with Server Accept |
| CS-RNG-O-2-13 | Seed RNG with Server Partial Acceptt |
| CS-RNG-O-3-13 | Seed RNG with Server Ignoret |
| CS-RNG-O-4-13 | Seed RNG with Server Denyt |
| CS-AC-M-1-13 | Sign with Known Asymmetric Key |
| CS_AC-M-2-13 | Signature Verify with Known Asymmetric Key |
| CS-AC-M-3-13 | Sign and Signature Verify with Known Asymmetric Key |
| CS-AC-M-4-13 | MAC with Known Key |
| CS_AC-M-5-13 | MAC Verify with Known Key |
| CS-AC-M-6-13 | MAC and MAC Verify with Known Key |
| CS-AC-M-7-13 | Hash |
| CS-AC-M-8-13 | Sign and Signature Verify with Known Asymmetric Key Date Checks |
KMIP Version 1.4 - Test Cases Supported
| Test Case | Description |
|---|---|
| AX-M-1-14 | Two key encryption |
| AX-M-2-14 | Two key encryption |
| TC-CERTATTR-1-14 | Certificate attributes |
| TC-CREG-2-14 | Client Registration |
| TC-CS-CORVAL-1-14 | Server/Client correlation values |
| TC-CREATE-SD-1-14 | Create Secret Data Object |
| TC-DERIVEKEY-1-14 | Derive Symmetric Key |
| TC-DERIVEKEY-2-14 | Derive Symmetric Key |
| TC-DERIVEKEY-3-14 | Derive Symmetric Key |
| TC-DERIVEKEY-4-14 | Derive Symmetric Key |
| TC-DERIVEKEY-5-14 | Derive Symmetric Key |
| TC-DERIVEKEY-6-14 | Derive Symmetric Key |
| TC-I18N-1-14 | UTF8 character in attribute |
| TC-I18N-2-14 | UTF8 character in attribute |
| TC-I18N-3-14 | UTF8 character in attribute |
| TC-ECDSA-SIGN-1-14 | ECC Key Pair Sign |
| TC-ECDSA-SIGN-DIGESTEDDATA-1-14 | ECC Key Pair Sign Digested |
| TC-RSA-SIGN-DIGESTEDDATA-1-14 | RSA Key Pair Sign Digested |
| TC-PKCS12-1-14 | PKCS#12 Private Key Export |
| TC-PKCS12-2-14 | PKCS#12 Private Key Export |
| TC_STREAM_SIGN_1_14 | Stream Sign with Asymmetric key |
| TC-STREAM-SIGNVFY-1-14 | Stream Sign Verify |
| TC-REKEY-1-14 | Rekey multiple times |
| CS-BC-M-GCM-1-14 | Encrypt/Decrypt Symmetric Key in GCM |
| CS-BC-M-GCM-2-14 | Encrypt/Decrypt Symmetric Key in GCM |
| CS-BC-M-GCM-3-14 | Encrypt/Decrypt Symmetric Key in GCM |
| CS-AC-OAEP-1-14 | Encrypt OAEP with known Asymmetric key |
| CS-AC-OAEP-2-14 | Decrypt OAEP with known Asymmetric key |
| CS-AC-OAEP-3-14 | Encrypt OAEP with known Asymmetric key |
| CS-AC-OAEP-4-14 | Decrypt OAEP with known Asymmetric key |
| CS-AC-OAEP-5-14 | Encrypt OAEP with known Asymmetric key |
| CS-AC-OAEP-6-14 | Decrypt OAEP with known Asymmetric key |
| CS-AC-OAEP-7-14 | Encrypt OAEP with known Asymmetric key |
| CS-AC-OAEP-8-14 | Decrypt OAEP with known Asymmetric key |
| CS-AC-OAEP-9-14 | Encrypt OAEP with known Asymmetric key |
| CS-AC-OAEP-10-14 | Decrypt OAEP with known Asymmetric key |
| TC-ECC-1-14 | |
| TC-ECC-2-14 | |
| TC-ECC-3-14 | |
| TC-EXTRACTABLE-1-14 | |
| TC-SENSITIVE-1-14 | |
| TC-MDO-1-14 | |
| TC-MDO-2-14 | |
| TC-MDO-3-14 | |
| TC-NP-1-14 | |
| TC-NP-2-14 | |
| TC-OFFSET-1-14 | |
| TC-OFFSET-2-14 | |
| TC-OTP-1-14 | |
| TC-OTP-2-14 | |
| TC-OTP-3-14 | |
| TC-OTP-4-14 | |
| TC-OTP-5-14 | |
| TC-PGP-1-14 | |
| TC-Q-CAP-1-14 | |
| TC-Q-CAP-2-14 | |
| TC-Q-CAP-3-14 | |
| TC-Q-CREG-1-14 | |
| TC-Q-PROF-1-14 | |
| TC-Q-PROF-2-14 | |
| TC-Q-PROF-3-14 | |
| TC-Q-RNGS-1-14 | |
| TC-Q-RNGS-2-14 | |
| TC-Q-RNGS-3-14 | |
| TC-Q-RNGS-4-14 | |
| TC-Q-RNGS-5-14 | |
| TC-Q-RNGS-6-14 | |
| TC-Q-S2C-1-14 | |
| TC-Q-S2C-2-14 | |
| TC-Q-S2C-PROF-1-14 | |
| TC-Q-VAL-1-14 | |
| TC-Q-VAL-2-14 | |
| TC-RNG-ATTR-1-14 | |
| TC-RNG-ATTR-2-14 | |
| TC-SJ-1-14 | |
| TC-SJ-2-14 | |
| TC-SJ-3-14 | |
| TC-SJ-4-14 | |
| TC-STREAM-ENC-1-14 | |
| TC-STREAM-ENC-2-14 | |
| TC-STREAM-ENCDEC-1-14 | |
| TC-STREAM-HASH-1-14 | |
| TC-STREAM-HASH-2-14 | |
| TC-STREAM-HASH-3-14 | |
| TC-STREAM-MAC-1-14 | |
| TC-STREAM-SIGN-1-14 | |
| TC-STREAM-SIGNVFY-1-14 | |
| TC-WRAP-1-14 | |
| TC-WRAP-2-14 | |
| TC-WRAP-3-14 | |
| CS-AC-M-1-14 | |
| CS-AC-M-2-14 | |
| CS-AC-M-3-14 | |
| CS-AC-M-4-14 | |
| CS-AC-M-5-14 | |
| CS-AC-M-6-14 | |
| CS-AC-M-7-14 | |
| CS-AC-M-8-14 | |
| CS-BC-M-1-14 | |
| CS-BC-M-2-14 | |
| CS-BC-M-3-14 | |
| CS-BC-M-4-14 | |
| CS-BC-M-5-14 | |
| CS-BC-M-6-14 | |
| CS-BC-M-7-14 | |
| CS-BC-M-8-14 | |
| CS-BC-M-9-14 | |
| CS-BC-M-10-14 | |
| CS-BC-M-11-14 | |
| CS-BC-M-12-14 | |
| CS-BC-M-13-14 | |
| CS-BC-M-14-14 | |
| CS-RNG-M-1-14 | |
| MSGENC-HTTPS-M-1-14 | |
| MSGENC-XML-M-1-14 | |
| MSGENC-JSON-M-1-14 | |
| OMOS-M-1-14 | |
| SASED-M-1-14 | |
| SASED-M-2-14 | |
| SASED-M-3-14 | |
| AKLC-M-1-14 | |
| AKLC-M-2-14 | |
| AKLC-M-3-14 | |
| SKLC-M-1-14 | |
| SKLC-M-2-14 | |
| SKLC-M-3-14 | |
| SKFF-M-1-14 | |
| SKFF-M-2-14 | |
| SKFF-M-3-14 | |
| SKFF-M-4-14 | |
| SKFF-M-5-14 | |
| SKFF-M-6-14 | |
| SKFF-M-7-14 | |
| SKFF-M-8-14 | |
| SKFF-M-9-14 | |
| SKFF-M-10-14 | |
| SKFF-M-11-14 | |
| SKFF-M-12-14 | |
| SUITEB-128-M-1-14 | |
| SUITEB-192-M-1-14 | |
| TL-M-1-14 | |
| TL-M-2-14 | |
| TL-M-3-14 |
KMIP Version 2.0 - Test Cases Supported
| Test Case |
|---|
| AX-M-1-20 |
| AX-M-2-20 |
| TC-CERTATTR-1-20 |
| TC-CREATE-SD-1-20 |
| TC-CS-CORVAL-1-20 |
| TC-DERIVEKEY-1-20 |
| TC-DERIVEKEY-2-20 |
| TC-DERIVEKEY-3-20 |
| TC-DERIVEKEY-4-20 |
| TC-DERIVEKEY-5-20 |
| TC-DERIVEKEY-6-20 |
| TC-ECC-1-20 |
| TC-ECC-2-20 |
| TC-ECC-3-20 |
| TC-ECDSA-SIGN-1-20 |
| TC-ECDSA-SIGN-DIGESTEDDATA-1-20 |
| TC-EXTRACTABLE-1-20 |
| TC-I18N-1-20 |
| TC-I18N-2-20 |
| TC-I18N-3-20 |
| TC-MDO-1-20 |
| TC-MDO-2-20 |
| TC-MDO-3-20 |
| TC-OFFSET-1-20 |
| TC-OFFSET-2-20 |
| TC-PGP-1-20 |
| TC-PKCS12-1-20 |
| TC-PKCS12-2-20 |
| TC-REKEY-1-20 |
| TC-RNG-ATTR-1-20 |
| TC-RNG-ATTR-2-20 |
| TC-RSA-SIGN-DIGESTEDDATA-1-20 |
| TC-SENSITIVE-1-20 |
| TC-STREAM-ENC-1-20 |
| TC-STREAM-ENC-2-20 |
| TC-STREAM-ENCDEC-1-20 |
| TC-STREAM-HASH-1-20 |
| TC-STREAM-HASH-2-20 |
| TC-STREAM-HASH-3-20 |
| TC-STREAM-MAC-1-20 |
| TC-STREAM-SIGN-1-20 |
| TC-STREAM-SIGNVFY-1-20 |
| CS-AC-M-1-20 |
| CS-AC-M-2-20 |
| CS-AC-M-3-20 |
| CS-AC-M-4-20 |
| CS-AC-M-5-20 |
| CS-AC-M-6-20 |
| CS-AC-M-7-20 |
| CS-AC-M-8-20 |
| CS-AC-OAEP-1-20 |
| CS-AC-OAEP-2-20 |
| CS-AC-OAEP-3-20 |
| CS-AC-OAEP-4-20 |
| CS-AC-OAEP-5-20 |
| CS-AC-OAEP-6-20 |
| CS-AC-OAEP-7-20 |
| CS-AC-OAEP-8-20 |
| CS-AC-OAEP-9-20 |
| CS-AC-OAEP-10-20 |
| CS-BC-M-1-20 |
| CS-BC-M-2-20 |
| CS-BC-M-3-20 |
| CS-BC-M-4-20 |
| CS-BC-M-5-20 |
| CS-BC-M-6-20 |
| CS-BC-M-7-20 |
| CS-BC-M-8-20 |
| CS-BC-M-9-20 |
| CS-BC-M-10-20 |
| CS-BC-M-11-20 |
| CS-BC-M-12-20 |
| CS-BC-M-13-20 |
| CS-BC-M-14-20 |
| CS-BC-M-GCM-1-20 |
| CS-BC-M-GCM-2-20 |
| CS-BC-M-GCM-3-20 |
| CS-RNG-M-1-20 |
| MSGENC-HTTPS-M-1-20 |
| MSGENC-XML-M-1-20 |
| MSGENC-JSON-M-1-20 |
| OMOS-M-1-20 |
| SASED-M-1-20 |
| SASED-M-2-20 |
| SASED-M-3-20 |
| AKLC-M-1-20 |
| AKLC-M-2-20 |
| AKLC-M-3-20 |
| SKLC-M-1-20 |
| SKLC-M-2-20 |
| SKLC-M-3-20 |
| SKFF-M-1-20 |
| SKFF-M-2-20 |
| SKFF-M-3-20 |
| SKFF-M-4-20 |
| SKFF-M-5-20 |
| SKFF-M-6-20 |
| SKFF-M-7-20 |
| SKFF-M-8-20 |
| SKFF-M-9-20 |
| SKFF-M-10-20 |
| SKFF-M-11-20 |
| SKFF-M-12-20 |
| TL-M-1-20 |
| TL-M-2-20 |
| TL-M-3-20 |
KMIP Version 2.1 - Test Cases Supported
| Test Case |
|---|
| TC-ASYNC-1-21 |
| TC-ASYNC-2-21 |
| TC-ASYNC-3-21 |
| TC-ASYNC-4-21 |
| TC-ASYNC-5-21 |
| TC-ASYNC-6-21 |
| TC-ASYNC-7-21 |
| TC-ASYNC-8-21 |
| TC-ASYNC-9-21 |
| TC-ASYNC-10-21 |
| TC-CERTATTR-1-21 |
| TC-CREATE-SD-1-21 |
| TC-CS-CORVAL-1-21 |
| TC-DERIVEKEY-1-21 |
| TC-DERIVEKEY-2-21 |
| TC-DERIVEKEY-3-21 |
| TC-DERIVEKEY-4-21 |
| TC-DERIVEKEY-5-21 |
| TC-DERIVEKEY-6-21 |
| TC-DIGESTS-1-21 |
| TC-DLOGIN-1-21 |
| TC-DLOGIN-2-21 |
| TC-DLOGIN-3-21 |
| TC-DLOGIN-4-21 |
| TC-DLOGIN-5-21 |
| TC-DLOGIN-6-21 |
| TC-DLOGIN-7-21 |
| TC-DLOGIN-8-21 |
| TC-DLOGIN-9-21 |
| TC-DLOGIN-10-21 |
| TC-DLOGIN-11-21 |
| TC-DLOGIN-12-21 |
| TC-DLOGIN-13-21 |
| TC-LOGIN-1-21 |
| TC-LOGIN-2-21 |
| TC-LOGIN-3-21 |
| TC-ECC-1-21 |
| TC-ECC-2-21 |
| TC-ECC-3-21 |
| TC-ECDSA-SIGN-1-21 |
| TC-ECDSA-SIGN-DIGESTEDDATA-1-21 |
| TC-EXTRACTABLE-1-21 |
| TC-I18N-1-21 |
| TC-I18N-2-21 |
| TC-I18N-3-21 |
| TC-IMPEXP-1-21 |
| TC-IMPEXP-2-21 |
| TC-IMPEXP-3-21 |
| TC-IMPEXP-4-21 |
| TC-IMPEXP-5-21 |
| TC-MD-1-21 |
| TC-MD-2-21 |
| TC-MD-3-21 |
| TC-MD-4-21 |
| TC-MD-5-21 |
| TC-MD-6-21 |
| TC-MD-21-21 |
| TC-MD-22-21 |
| TC-MD-23-21 |
| TC-MD-24-21 |
| TC-MDO-1-21 |
| TC-MDO-2-21 |
| TC-MDO-3-21 |
| TC-OFFSET-1-21 |
| TC-OFFSET-2-21 |
| TC-PGP-1-21 |
| TC-PING-1-21 |
| TC-PKCS12-1-21 |
| TC-PKCS12-2-21 |
| TC-REENCRYPT-1-21 |
| TC-REENCRYPT-2-21 |
| TC-REKEY-1-21 |
| TC-REKEY-2-21 |
| TC-REKEY-3-21 |
| TC-REKEY-4-21 |
| TC-REKEY-5-21 |
| TC-REKEY-6-21 |
| TC-REKEY-7-21 |
| TC-REKEY-8-21 |
| TC-REKEY-9-21 |
| TC-REKEY-10-21 |
| TC-REKEY-11-21 |
| TC-RNG-ATTR-1-21 |
| TC-RNG-ATTR-2-21 |
| TC-RSA-SIGN-DIGESTEDDATA-1-21 |
| TC-SENSITIVE-1-21 |
| TC-SETATTR-1-21 |
| TC-SETATTR-2-21 |
| TC-SETATTR-3-21 |
| TC-SJ-1-21 |
| TC-SJ-2-21 |
| TC-SJ-3-21 |
| TC-SJ-4-21 |
| TC-STREAM-ENC-1-21 |
| TC-STREAM-ENC-2-21 |
| TC-STREAM-ENCDEC-1-21 |
| TC-STREAM-HASH-1-21 |
| TC-STREAM-HASH-2-21 |
| TC-STREAM-HASH-3-21 |
| TC-STREAM-MAC-1-21 |
| TC-STREAM-SIGN-1-21 |
| TC-STREAM-SIGNVFY-1-21 |
| TC-WRAP-1-21 |
| TC-WRAP-2-21 |
| TC-WRAP-3-21 |
| BL-M-1-21 |
| BL-M-2-21 |
| BL-M-3-21 |
| BL-M-4-21 |
| BL-M-5-21 |
| BL-M-6-21 |
| BL-M-7-21 |
| BL-M-8-21 |
| BL-M-9-21 |
| BL-M-10-21 |
| BL-M-11-21 |
| BL-M-12-21 |
| BL-M-13-21 |
| CS-AC-M-1-21 |
| CS-AC-M-2-21 |
| CS-AC-M-3-21 |
| CS-AC-M-4-21 |
| CS-AC-M-5-21 |
| CS-AC-M-6-21 |
| CS-AC-M-7-21 |
| CS-AC-M-8-21 |
| CS-AC-OAEP-1-21 |
| CS-AC-OAEP-2-21 |
| CS-AC-OAEP-3-21 |
| CS-AC-OAEP-4-21 |
| CS-AC-OAEP-5-21 |
| CS-AC-OAEP-6-21 |
| CS-AC-OAEP-7-21 |
| CS-AC-OAEP-8-21 |
| CS-AC-OAEP-9-21 |
| CS-AC-OAEP-10-21 |
| CS-BC-M-1-21 |
| CS-BC-M-2-21 |
| CS-BC-M-3-21 |
| CS-BC-M-4-21 |
| CS-BC-M-5-21 |
| CS-BC-M-6-21 |
| CS-BC-M-7-21 |
| CS-BC-M-8-21 |
| CS-BC-M-9-21 |
| CS-BC-M-10-21 |
| CS-BC-M-11-21 |
| CS-BC-M-12-21 |
| CS-BC-M-13-21 |
| CS-BC-M-14-21 |
| CS-BC-M-CHACHA20-1-21 |
| CS-BC-M-CHACHA20-2-21 |
| CS-BC-M-CHACHA20-3-21 |
| CS-BC-M-CHACHA20POLY1305-1-21 |
| CS-BC-M-GCM-1-21 |
| CS-BC-M-GCM-2-21 |
| CS-BC-M-GCM-3-21 |
| CS-RNG-M-1-21 |
| CS-RNG-O-1-21 |
| CS-RNG-O-2-21 |
| CS-RNG-O-3-21 |
| CS-RNG-O-4-21 |
| MSGENC-HTTPS-M-1-21 |
| MSGENC-XML-M-1-21 |
| MSGENC-JSON-M-1-21 |
| OMOS-M-1-21 |
| OMOS-O-1-21 |
| PKCS11-M-1-21 |
| QS-M-1-21 |
| QS-M-2-21 |
| SASED-M-1-21 |
| SASED-M-2-21 |
| SASED-M-3-21 |
| AKLC-M-1-21 |
| AKLC-M-2-21 |
| AKLC-M-3-21 |
| AKLC-0-1-21 |
| SKLC-M-1-21 |
| SKLC-M-2-21 |
| SKLC-M-3-21 |
| SKLC-O-1-21 |
| SKFF-M-1-21 |
| SKFF-M-2-21 |
| SKFF-M-3-21 |
| SKFF-M-4-21 |
| SKFF-M-5-21 |
| SKFF-M-6-21 |
| SKFF-M-7-21 |
| SKFF-M-8-21 |
| SKFF-M-9-21 |
| SKFF-M-10-21 |
| SKFF-M-11-21 |
| SKFF-M-12-21 |
| TL-M-1-21 |
| TL-M-2-21 |
| TL-M-3-21 |
KMIP Version 3.0 - Test Cases Supported
| AKLC_M_1_30 |
| AKLC_M_2_30 |
| AKLC_M_3_30 |
| AKLC_O_1_30 |
| AX_M_1_30 |
| AX_M_2_30 |
| BL_M_1_30 |
| BL_M_2_30 |
| BL_M_3_30 |
| BL_M_4_30 |
| BL_M_5_30 |
| BL_M_6_30 |
| BL_M_7_30 |
| BL_M_8_30 |
| BL_M_9_30 |
| BL_M_10_30 |
| BL_M_11_30 |
| BL_M_12_30 |
| BL_M_13_30 |
| BL_M_14_30 |
| BL_M_15_30 |
| BL_M_16_30 |
| BL_M_17_30 |
| BL_M_18_30 |
| BL_M_19_30 |
| BL_M_20_30 |
| BL_M_21_30 |
| CS_AC_M_1_30 |
| CS_AC_M_2_30 |
| CS_AC_M_3_30 |
| CS_AC_M_4_30 |
| CS_AC_M_5_30 |
| CS_AC_M_6_30 |
| CS_AC_M_7_30 |
| CS_AC_M_8_30 |
| CS_AC_OAEP_1_30 |
| CS_AC_OAEP_2_30 |
| CS_AC_OAEP_3_30 |
| CS_AC_OAEP_4_30 |
| CS_AC_OAEP_5_30 |
| CS_AC_OAEP_6_30 |
| CS_AC_OAEP_7_30 |
| CS_AC_OAEP_8_30 |
| CS_AC_OAEP_9_30 |
| CS_AC_OAEP_10_30 |
| CS_BC_M_1_30 |
| CS_BC_M_2_30 |
| CS_BC_M_3_30 |
| CS_BC_M_4_30 |
| CS_BC_M_5_30 |
| CS_BC_M_6_30 |
| CS_BC_M_7_30 |
| CS_BC_M_8_30 |
| CS_BC_M_9_30 |
| CS_BC_M_10_30 |
| CS_BC_M_11_30 |
| CS_BC_M_12_30 |
| CS_BC_M_13_30 |
| CS_BC_M_14_30 |
| CS_BC_M_GCM_1_30 |
| CS_BC_M_GCM_2_30 |
| CS_BC_M_GCM_3_30 |
| CS_BC_M_CHACHA20_1_30 |
| CS_BC_M_CHACHA20_2_30 |
| CS_BC_M_CHACHA20_3_30 |
| CS_BC_M_CHACHA20_4_30 |
| CS_BC_M_CHACHA20POLY1305_1_30 |
| CS_RNG_M_1_30 |
| CS_RNG_O_1_30 |
| CS_RNG_O_2_30 |
| CS_RNG_O_3_30 |
| CS_RNG_O_4_30 |
| MSGENC_HTTPS_M_1_30 |
| MSGENC_XML_M_1_30 |
| MSGENC_JSON_M_1_30 |
| OMOS_M_1_30 |
| OMOS_O_1_30 |
| PKCS11_M_1_30 |
| QS_M_1_30 |
| QS_M_2_30 |
| SASED_M_1_30 |
| SASED_M_2_30 |
| SASED_M_3_30 |
| SKFF_M_1_30 |
| SKFF_M_2_30 |
| SKFF_M_3_30 |
| SKFF_M_4_30 |
| SKFF_M_5_30 |
| SKFF_M_6_30 |
| SKFF_M_7_30 |
| SKFF_M_8_30 |
| SKFF_M_9_30 |
| SKFF_M_10_30 |
| SKFF_M_11_30 |
| SKFF_M_12_30 |
| SKLC_M_1_30 |
| SKLC_M_2_30 |
| SKLC_M_3_30 |
| SKLC_O_1_30 |
| TC_ADJUSTATTR_1_30 |
| TC_ADJUSTATTR_2_30 |
| TC_ADJUSTATTR_3_30 |
| TC_ADJUSTATTR_4_30 |
| TC_ADJUSTATTR_5_30 |
| TC_AESXTS_1_30 |
| TC_ASYNC_1_30 |
| TC_ASYNC_2_30 |
| TC_ASYNC_3_30 |
| TC_ASYNC_4_30 |
| TC_ASYNC_5_30 |
| TC_ASYNC_6_30 |
| TC_ASYNC_7_30 |
| TC_ASYNC_8_30 |
| TC_ASYNC_9_30 |
| TC_ASYNC_10_30 |
| TC_CERTATTR_1_30 |
| TC_CREATE_SD_1_30 |
| TC_CREG_1_30 |
| TC_CREG_2_30 |
| TC_CREG_3_30 |
| TC_CS_CORVAL_1_30 |
| TC_DERIVEKEY_1_30 |
| TC_DERIVEKEY_2_30 |
| TC_DERIVEKEY_3_30 |
| TC_DERIVEKEY_4_30 |
| TC_DERIVEKEY_5_30 |
| TC_DERIVEKEY_6_30 |
| TC_DIGESTS_1_30 |
| TC_DLOGIN_1_30 |
| TC_DLOGIN_2_30 |
| TC_DLOGIN_3_30 |
| TC_DLOGIN_4_30 |
| TC_DLOGIN_5_30 |
| TC_DLOGIN_6_30 |
| TC_DLOGIN_7_30 |
| TC_DLOGIN_8_30 |
| TC_DLOGIN_9_30 |
| TC_DLOGIN_10_30 |
| TC_DLOGIN_11_30 |
| TC_DLOGIN_12_30 |
| TC_DLOGIN_13_30 |
| TC_ECC_1_30 |
| TC_ECC_2_30 |
| TC_ECC_3_30 |
| TC_ECDSA_SIGN_1_30 |
| TC_ECDSA_SIGN_DIGESTEDDATA_1_30 |
| TC_EXTRACTABLE_1_30 |
| TC_I18N_1_30 |
| TC_I18N_2_30 |
| TC_I18N_3_30 |
| TC_IMPEXP_1_30 |
| TC_IMPEXP_2_30 |
| TC_IMPEXP_3_30 |
| TC_IMPEXP_4_30 |
| TC_IMPEXP_5_30 |
| TC_LOGIN_1_30 |
| TC_LOGIN_2_30 |
| TC_LOGIN_3_30 |
| TC_MD_1_30 |
| TC_MD_2_30 |
| TC_MD_3_30 |
| TC_MD_4_30 |
| TC_MD_5_30 |
| TC_MD_6_30 |
| TC_MD_21_30 |
| TC_MD_22_30 |
| TC_MD_23_30 |
| TC_MD_24_30 |
| TC_MDO_1_30 |
| TC_MDO_2_30 |
| TC_MDO_3_30 |
| TC_OFFSET_1_30 |
| TC_OFFSET_2_30 |
| TC_OTP_1_30 |
| TC_OTP_2_30 |
| TC_OTP_3_30 |
| TC_OTP_4_30 |
| TC_OTP_5_30 |
| TC_PGP_1_30 |
| TC_PING_1_30 |
| TC_PKCS12_1_30 |
| TC_PKCS12_2_30 |
| TC_PKCS12_3_30 |
| TC_Q_CAP_1_30 |
| TC_Q_CAP_2_30 |
| TC_Q_CREG_1_30 |
| TC_Q_PROF_1_30 |
| TC_Q_PROF_2_30 |
| TC_Q_PROF_3_30 |
| TC_Q_RNGS_1_30 |
| TC_Q_RNGS_2_30 |
| TC_Q_RNGS_3_30 |
| TC_Q_RNGS_4_30 |
| TC_Q_RNGS_5_30 |
| TC_Q_RNGS_6_30 |
| TC_Q_S2C_1_30 |
| TC_Q_S2C_2_30 |
| TC_Q_S2C_PROF_1_30 |
| TC_Q_S2C_PROF_2_30 |
| TC_Q_VAL_1_30 |
| TC_Q_VAL_2_30 |
| TC_REENCRYPT_1_30 |
| TC_REENCRYPT_2_30 |
| TC_REENCRYPT_3_30 |
| TC_REENCRYPT_4_30 |
| TC_REENCRYPT_5_30 |
| TC_REENCRYPT_6_30 |
| TC_REKEY_1_30 |
| TC_REKEY_2_30 |
| TC_REKEY_3_30 |
| TC_REKEY_4_30 |
| TC_REKEY_5_30 |
| TC_REKEY_6_30 |
| TC_REKEY_7_30 |
| TC_REKEY_8_30 |
| TC_REKEY_9_30 |
| TC_REKEY_10_30 |
| TC_REKEY_11_30 |
| TC_REKEY_12_30 |
| TC_RNG_ATTR_1_30 |
| TC_RNG_ATTR_2_30 |
| TC_RSA_SIGN_DIGESTEDDATA_1_30 |
| TC_SENSITIVE_1_30 |
| TC_SETATTR_1_30 |
| TC_SETATTR_2_30 |
| TC_SETATTR_3_30 |
| TC_SETATTR_4_30 |
| TC_SJ_1_30 |
| TC_SJ_2_30 |
| TC_SJ_3_30 |
| TC_SJ_4_30 |
| TC_SJ_5_30 |
| TC_SJ_6_30 |
| TC_STREAM_ENC_1_30 |
| TC_STREAM_ENC_2_30 |
| TC_STREAM_ENCDEC_1_30 |
| TC_STREAM_HASH_1_30 |
| TC_STREAM_HASH_2_30 |
| TC_STREAM_HASH_3_30 |
| TC_STREAM_MAC_1_30 |
| TC_STREAM_SIGN_1_30 |
| TC_STREAM_SIGNVFY_1_30 |
| TC_WRAP_1_30 |
| TC_WRAP_2_30 |
| TC_WRAP_3_30 |
| TL_M_1_30 |
| TL_M_2_30 |
| TL_M_3_30 |
KMIP Version 3.0 - PQC test cases
| ML-DSA-44-keygen-1-30 |
| ML-DSA-44-keygen-2-30 |
| ML-DSA-44-keygen-3-30 |
| ML-DSA-44-keygen-4-30 |
| ML-DSA-44-keygen-5-30 |
| ML-DSA-44-keygen-6-30 |
| ML-DSA-44-keygen-7-30 |
| ML-DSA-44-keygen-8-30 |
| ML-DSA-44-keygen-9-30 |
| ML-DSA-44-keygen-10-30 |
| ML-DSA-44-keygen-11-30 |
| ML-DSA-44-keygen-12-30 |
| ML-DSA-44-keygen-13-30 |
| ML-DSA-44-keygen-14-30 |
| ML-DSA-44-keygen-15-30 |
| ML-DSA-44-keygen-16-30 |
| ML-DSA-44-keygen-17-30 |
| ML-DSA-44-keygen-18-30 |
| ML-DSA-44-keygen-19-30 |
| ML-DSA-44-keygen-20-30 |
| ML-DSA-44-keygen-21-30 |
| ML-DSA-44-keygen-22-30 |
| ML-DSA-44-keygen-23-30 |
| ML-DSA-44-keygen-24-30 |
| ML-DSA-44-keygen-25-30 |
| ML-DSA-44-siggen-1-30 |
| ML-DSA-44-siggen-2-30 |
| ML-DSA-44-siggen-3-30 |
| ML-DSA-44-siggen-4-30 |
| ML-DSA-44-siggen-5-30 |
| ML-DSA-44-siggen-6-30 |
| ML-DSA-44-siggen-7-30 |
| ML-DSA-44-siggen-8-30 |
| ML-DSA-44-siggen-9-30 |
| ML-DSA-44-siggen-10-30 |
| ML-DSA-44-siggen-11-30 |
| ML-DSA-44-siggen-12-30 |
| ML-DSA-44-siggen-13-30 |
| ML-DSA-44-siggen-14-30 |
| ML-DSA-44-siggen-15-30 |
| ML-DSA-44-siggen-91-30 |
| ML-DSA-44-siggen-92-30 |
| ML-DSA-44-siggen-93-30 |
| ML-DSA-44-siggen-94-30 |
| ML-DSA-44-siggen-95-30 |
| ML-DSA-44-siggen-96-30 |
| ML-DSA-44-siggen-97-30 |
| ML-DSA-44-siggen-98-30 |
| ML-DSA-44-siggen-99-30 |
| ML-DSA-44-siggen-100-30 |
| ML-DSA-44-siggen-101-30 |
| ML-DSA-44-siggen-102-30 |
| ML-DSA-44-siggen-103-30 |
| ML-DSA-44-siggen-104-30 |
| ML-DSA-44-siggen-105-30 |
| ML-DSA-44-siggen-106-30 |
| ML-DSA-44-siggen-107-30 |
| ML-DSA-44-siggen-108-30 |
| ML-DSA-44-siggen-109-30 |
| ML-DSA-44-siggen-110-30 |
| ML-DSA-44-siggen-111-30 |
| ML-DSA-44-siggen-112-30 |
| ML-DSA-44-siggen-113-30 |
| ML-DSA-44-siggen-114-30 |
| ML-DSA-44-siggen-115-30 |
| ML-DSA-44-siggen-116-30 |
| ML-DSA-44-siggen-117-30 |
| ML-DSA-44-siggen-118-30 |
| ML-DSA-44-siggen-119-30 |
| ML-DSA-44-siggen-120-30 |
| ML-DSA-44-siggen-181-30 |
| ML-DSA-44-siggen-182-30 |
| ML-DSA-44-siggen-183-30 |
| ML-DSA-44-siggen-184-30 |
| ML-DSA-44-siggen-185-30 |
| ML-DSA-44-siggen-186-30 |
| ML-DSA-44-siggen-187-30 |
| ML-DSA-44-siggen-188-30 |
| ML-DSA-44-siggen-189-30 |
| ML-DSA-44-siggen-190-30 |
| ML-DSA-44-siggen-191-30 |
| ML-DSA-44-siggen-192-30 |
| ML-DSA-44-siggen-193-30 |
| ML-DSA-44-siggen-194-30 |
| ML-DSA-44-siggen-195-30 |
| ML-DSA-44-siggen-271-30 |
| ML-DSA-44-siggen-272-30 |
| ML-DSA-44-siggen-273-30 |
| ML-DSA-44-siggen-274-30 |
| ML-DSA-44-siggen-275-30 |
| ML-DSA-44-siggen-276-30 |
| ML-DSA-44-siggen-277-30 |
| ML-DSA-44-siggen-278-30 |
| ML-DSA-44-siggen-279-30 |
| ML-DSA-44-siggen-280-30 |
| ML-DSA-44-siggen-281-30 |
| ML-DSA-44-siggen-282-30 |
| ML-DSA-44-siggen-283-30 |
| ML-DSA-44-siggen-284-30 |
| ML-DSA-44-siggen-285-30 |
| ML-DSA-44-siggen-286-30 |
| ML-DSA-44-siggen-287-30 |
| ML-DSA-44-siggen-288-30 |
| ML-DSA-44-siggen-289-30 |
| ML-DSA-44-siggen-290-30 |
| ML-DSA-44-siggen-291-30 |
| ML-DSA-44-siggen-292-30 |
| ML-DSA-44-siggen-293-30 |
| ML-DSA-44-siggen-294-30 |
| ML-DSA-44-siggen-295-30 |
| ML-DSA-44-siggen-296-30 |
| ML-DSA-44-siggen-297-30 |
| ML-DSA-44-siggen-298-30 |
| ML-DSA-44-siggen-299-30 |
| ML-DSA-44-siggen-300-30 |
| ML-DSA-44-sigver-1-30 |
| ML-DSA-44-sigver-2-30 |
| ML-DSA-44-sigver-3-30 |
| ML-DSA-44-sigver-4-30 |
| ML-DSA-44-sigver-5-30 |
| ML-DSA-44-sigver-6-30 |
| ML-DSA-44-sigver-7-30 |
| ML-DSA-44-sigver-8-30 |
| ML-DSA-44-sigver-9-30 |
| ML-DSA-44-sigver-10-30 |
| ML-DSA-44-sigver-11-30 |
| ML-DSA-44-sigver-12-30 |
| ML-DSA-44-sigver-13-30 |
| ML-DSA-44-sigver-14-30 |
| ML-DSA-44-sigver-15-30 |
| ML-DSA-44-sigver-91-30 |
| ML-DSA-44-sigver-92-30 |
| ML-DSA-44-sigver-93-30 |
| ML-DSA-44-sigver-94-30 |
| ML-DSA-44-sigver-95-30 |
| ML-DSA-44-sigver-96-30 |
| ML-DSA-44-sigver-97-30 |
| ML-DSA-44-sigver-98-30 |
| ML-DSA-44-sigver-99-30 |
| ML-DSA-44-sigver-100-30 |
| ML-DSA-44-sigver-101-30 |
| ML-DSA-44-sigver-102-30 |
| ML-DSA-44-sigver-103-30 |
| ML-DSA-44-sigver-104-30 |
| ML-DSA-44-sigver-105-30 |
| ML-DSA-44-sigver-106-30 |
| ML-DSA-44-sigver-107-30 |
| ML-DSA-44-sigver-108-30 |
| ML-DSA-44-sigver-109-30 |
| ML-DSA-44-sigver-110-30 |
| ML-DSA-44-sigver-111-30 |
| ML-DSA-44-sigver-112-30 |
| ML-DSA-44-sigver-113-30 |
| ML-DSA-44-sigver-114-30 |
| ML-DSA-44-sigver-115-30 |
| ML-DSA-44-sigver-116-30 |
| ML-DSA-44-sigver-117-30 |
| ML-DSA-44-sigver-118-30 |
| ML-DSA-44-sigver-119-30 |
| ML-DSA-44-sigver-120-30 |
| ML-DSA-65-keygen-26-30 |
| ML-DSA-65-keygen-27-30 |
| ML-DSA-65-keygen-28-30 |
| ML-DSA-65-keygen-29-30 |
| ML-DSA-65-keygen-30-30 |
| ML-DSA-65-keygen-31-30 |
| ML-DSA-65-keygen-32-30 |
| ML-DSA-65-keygen-33-30 |
| ML-DSA-65-keygen-34-30 |
| ML-DSA-65-keygen-35-30 |
| ML-DSA-65-keygen-36-30 |
| ML-DSA-65-keygen-37-30 |
| ML-DSA-65-keygen-38-30 |
| ML-DSA-65-keygen-39-30 |
| ML-DSA-65-keygen-40-30 |
| ML-DSA-65-keygen-41-30 |
| ML-DSA-65-keygen-42-30 |
| ML-DSA-65-keygen-43-30 |
| ML-DSA-65-keygen-44-30 |
| ML-DSA-65-keygen-45-30 |
| ML-DSA-65-keygen-46-30 |
| ML-DSA-65-keygen-47-30 |
| ML-DSA-65-keygen-48-30 |
| ML-DSA-65-keygen-49-30 |
| ML-DSA-65-keygen-50-30 |
| ML-DSA-65-siggen-31-30 |
| ML-DSA-65-siggen-32-30 |
| ML-DSA-65-siggen-33-30 |
| ML-DSA-65-siggen-34-30 |
| ML-DSA-65-siggen-35-30 |
| ML-DSA-65-siggen-36-30 |
| ML-DSA-65-siggen-37-30 |
| ML-DSA-65-siggen-38-30 |
| ML-DSA-65-siggen-39-30 |
| ML-DSA-65-siggen-40-30 |
| ML-DSA-65-siggen-41-30 |
| ML-DSA-65-siggen-42-30 |
| ML-DSA-65-siggen-43-30 |
| ML-DSA-65-siggen-44-30 |
| ML-DSA-65-siggen-45-30 |
| ML-DSA-65-siggen-121-30 |
| ML-DSA-65-siggen-122-30 |
| ML-DSA-65-siggen-123-30 |
| ML-DSA-65-siggen-124-30 |
| ML-DSA-65-siggen-125-30 |
| ML-DSA-65-siggen-126-30 |
| ML-DSA-65-siggen-127-30 |
| ML-DSA-65-siggen-128-30 |
| ML-DSA-65-siggen-129-30 |
| ML-DSA-65-siggen-130-30 |
| ML-DSA-65-siggen-131-30 |
| ML-DSA-65-siggen-132-30 |
| ML-DSA-65-siggen-133-30 |
| ML-DSA-65-siggen-134-30 |
| ML-DSA-65-siggen-135-30 |
| ML-DSA-65-siggen-136-30 |
| ML-DSA-65-siggen-137-30 |
| ML-DSA-65-siggen-138-30 |
| ML-DSA-65-siggen-139-30 |
| ML-DSA-65-siggen-140-30 |
| ML-DSA-65-siggen-141-30 |
| ML-DSA-65-siggen-142-30 |
| ML-DSA-65-siggen-143-30 |
| ML-DSA-65-siggen-144-30 |
| ML-DSA-65-siggen-145-30 |
| ML-DSA-65-siggen-146-30 |
| ML-DSA-65-siggen-147-30 |
| ML-DSA-65-siggen-148-30 |
| ML-DSA-65-siggen-149-30 |
| ML-DSA-65-siggen-150-30 |
| ML-DSA-65-siggen-211-30 |
| ML-DSA-65-siggen-212-30 |
| ML-DSA-65-siggen-213-30 |
| ML-DSA-65-siggen-214-30 |
| ML-DSA-65-siggen-215-30 |
| ML-DSA-65-siggen-216-30 |
| ML-DSA-65-siggen-217-30 |
| ML-DSA-65-siggen-218-30 |
| ML-DSA-65-siggen-219-30 |
| ML-DSA-65-siggen-220-30 |
| ML-DSA-65-siggen-221-30 |
| ML-DSA-65-siggen-222-30 |
| ML-DSA-65-siggen-223-30 |
| ML-DSA-65-siggen-224-30 |
| ML-DSA-65-siggen-225-30 |
| ML-DSA-65-siggen-301-30 |
| ML-DSA-65-siggen-302-30 |
| ML-DSA-65-siggen-303-30 |
| ML-DSA-65-siggen-304-30 |
| ML-DSA-65-siggen-305-30 |
| ML-DSA-65-siggen-306-30 |
| ML-DSA-65-siggen-307-30 |
| ML-DSA-65-siggen-308-30 |
| ML-DSA-65-siggen-309-30 |
| ML-DSA-65-siggen-310-30 |
| ML-DSA-65-siggen-311-30 |
| ML-DSA-65-siggen-312-30 |
| ML-DSA-65-siggen-313-30 |
| ML-DSA-65-siggen-314-30 |
| ML-DSA-65-siggen-315-30 |
| ML-DSA-65-siggen-316-30 |
| ML-DSA-65-siggen-317-30 |
| ML-DSA-65-siggen-318-30 |
| ML-DSA-65-siggen-319-30 |
| ML-DSA-65-siggen-320-30 |
| ML-DSA-65-siggen-321-30 |
| ML-DSA-65-siggen-322-30 |
| ML-DSA-65-siggen-323-30 |
| ML-DSA-65-siggen-324-30 |
| ML-DSA-65-siggen-325-30 |
| ML-DSA-65-siggen-326-30 |
| ML-DSA-65-siggen-327-30 |
| ML-DSA-65-siggen-328-30 |
| ML-DSA-65-siggen-329-30 |
| ML-DSA-65-siggen-330-30 |
| ML-DSA-65-sigver-31-30 |
| ML-DSA-65-sigver-32-30 |
| ML-DSA-65-sigver-33-30 |
| ML-DSA-65-sigver-34-30 |
| ML-DSA-65-sigver-35-30 |
| ML-DSA-65-sigver-36-30 |
| ML-DSA-65-sigver-37-30 |
| ML-DSA-65-sigver-38-30 |
| ML-DSA-65-sigver-39-30 |
| ML-DSA-65-sigver-40-30 |
| ML-DSA-65-sigver-41-30 |
| ML-DSA-65-sigver-42-30 |
| ML-DSA-65-sigver-43-30 |
| ML-DSA-65-sigver-44-30 |
| ML-DSA-65-sigver-45-30 |
| ML-DSA-65-sigver-121-30 |
| ML-DSA-65-sigver-122-30 |
| ML-DSA-65-sigver-123-30 |
| ML-DSA-65-sigver-124-30 |
| ML-DSA-65-sigver-125-30 |
| ML-DSA-65-sigver-126-30 |
| ML-DSA-65-sigver-127-30 |
| ML-DSA-65-sigver-128-30 |
| ML-DSA-65-sigver-129-30 |
| ML-DSA-65-sigver-130-30 |
| ML-DSA-65-sigver-131-30 |
| ML-DSA-65-sigver-132-30 |
| ML-DSA-65-sigver-133-30 |
| ML-DSA-65-sigver-134-30 |
| ML-DSA-65-sigver-135-30 |
| ML-DSA-65-sigver-136-30 |
| ML-DSA-65-sigver-137-30 |
| ML-DSA-65-sigver-138-30 |
| ML-DSA-65-sigver-139-30 |
| ML-DSA-65-sigver-140-30 |
| ML-DSA-65-sigver-141-30 |
| ML-DSA-65-sigver-142-30 |
| ML-DSA-65-sigver-143-30 |
| ML-DSA-65-sigver-144-30 |
| ML-DSA-65-sigver-145-30 |
| ML-DSA-65-sigver-146-30 |
| ML-DSA-65-sigver-147-30 |
| ML-DSA-65-sigver-148-30 |
| ML-DSA-65-sigver-149-30 |
| ML-DSA-65-sigver-150-30 |
| ML-DSA-87-keygen-51-30 |
| ML-DSA-87-keygen-52-30 |
| ML-DSA-87-keygen-53-30 |
| ML-DSA-87-keygen-54-30 |
| ML-DSA-87-keygen-55-30 |
| ML-DSA-87-keygen-56-30 |
| ML-DSA-87-keygen-57-30 |
| ML-DSA-87-keygen-58-30 |
| ML-DSA-87-keygen-59-30 |
| ML-DSA-87-keygen-60-30 |
| ML-DSA-87-keygen-61-30 |
| ML-DSA-87-keygen-62-30 |
| ML-DSA-87-keygen-63-30 |
| ML-DSA-87-keygen-64-30 |
| ML-DSA-87-keygen-65-30 |
| ML-DSA-87-keygen-66-30 |
| ML-DSA-87-keygen-67-30 |
| ML-DSA-87-keygen-68-30 |
| ML-DSA-87-keygen-69-30 |
| ML-DSA-87-keygen-70-30 |
| ML-DSA-87-keygen-71-30 |
| ML-DSA-87-keygen-72-30 |
| ML-DSA-87-keygen-73-30 |
| ML-DSA-87-keygen-74-30 |
| ML-DSA-87-keygen-75-30 |
| ML-DSA-87-siggen-61-30 |
| ML-DSA-87-siggen-62-30 |
| ML-DSA-87-siggen-63-30 |
| ML-DSA-87-siggen-64-30 |
| ML-DSA-87-siggen-65-30 |
| ML-DSA-87-siggen-66-30 |
| ML-DSA-87-siggen-67-30 |
| ML-DSA-87-siggen-68-30 |
| ML-DSA-87-siggen-69-30 |
| ML-DSA-87-siggen-70-30 |
| ML-DSA-87-siggen-71-30 |
| ML-DSA-87-siggen-72-30 |
| ML-DSA-87-siggen-73-30 |
| ML-DSA-87-siggen-74-30 |
| ML-DSA-87-siggen-75-30 |
| ML-DSA-87-siggen-151-30 |
| ML-DSA-87-siggen-152-30 |
| ML-DSA-87-siggen-153-30 |
| ML-DSA-87-siggen-154-30 |
| ML-DSA-87-siggen-155-30 |
| ML-DSA-87-siggen-156-30 |
| ML-DSA-87-siggen-157-30 |
| ML-DSA-87-siggen-158-30 |
| ML-DSA-87-siggen-159-30 |
| ML-DSA-87-siggen-160-30 |
| ML-DSA-87-siggen-161-30 |
| ML-DSA-87-siggen-162-30 |
| ML-DSA-87-siggen-163-30 |
| ML-DSA-87-siggen-164-30 |
| ML-DSA-87-siggen-165-30 |
| ML-DSA-87-siggen-166-30 |
| ML-DSA-87-siggen-167-30 |
| ML-DSA-87-siggen-168-30 |
| ML-DSA-87-siggen-169-30 |
| ML-DSA-87-siggen-170-30 |
| ML-DSA-87-siggen-171-30 |
| ML-DSA-87-siggen-172-30 |
| ML-DSA-87-siggen-173-30 |
| ML-DSA-87-siggen-174-30 |
| ML-DSA-87-siggen-175-30 |
| ML-DSA-87-siggen-176-30 |
| ML-DSA-87-siggen-177-30 |
| ML-DSA-87-siggen-178-30 |
| ML-DSA-87-siggen-179-30 |
| ML-DSA-87-siggen-180-30 |
| ML-DSA-87-siggen-241-30 |
| ML-DSA-87-siggen-242-30 |
| ML-DSA-87-siggen-243-30 |
| ML-DSA-87-siggen-244-30 |
| ML-DSA-87-siggen-245-30 |
| ML-DSA-87-siggen-246-30 |
| ML-DSA-87-siggen-247-30 |
| ML-DSA-87-siggen-248-30 |
| ML-DSA-87-siggen-249-30 |
| ML-DSA-87-siggen-250-30 |
| ML-DSA-87-siggen-251-30 |
| ML-DSA-87-siggen-252-30 |
| ML-DSA-87-siggen-253-30 |
| ML-DSA-87-siggen-254-30 |
| ML-DSA-87-siggen-255-30 |
| ML-DSA-87-siggen-331-30 |
| ML-DSA-87-siggen-332-30 |
| ML-DSA-87-siggen-333-30 |
| ML-DSA-87-siggen-334-30 |
| ML-DSA-87-siggen-335-30 |
| ML-DSA-87-siggen-336-30 |
| ML-DSA-87-siggen-337-30 |
| ML-DSA-87-siggen-338-30 |
| ML-DSA-87-siggen-339-30 |
| ML-DSA-87-siggen-340-30 |
| ML-DSA-87-siggen-341-30 |
| ML-DSA-87-siggen-342-30 |
| ML-DSA-87-siggen-343-30 |
| ML-DSA-87-siggen-344-30 |
| ML-DSA-87-siggen-345-30 |
| ML-DSA-87-siggen-346-30 |
| ML-DSA-87-siggen-347-30 |
| ML-DSA-87-siggen-348-30 |
| ML-DSA-87-siggen-349-30 |
| ML-DSA-87-siggen-350-30 |
| ML-DSA-87-siggen-351-30 |
| ML-DSA-87-siggen-352-30 |
| ML-DSA-87-siggen-353-30 |
| ML-DSA-87-siggen-354-30 |
| ML-DSA-87-siggen-355-30 |
| ML-DSA-87-siggen-356-30 |
| ML-DSA-87-siggen-357-30 |
| ML-DSA-87-siggen-358-30 |
| ML-DSA-87-siggen-359-30 |
| ML-DSA-87-siggen-360-30 |
| ML-DSA-87-sigver-61-30 |
| ML-DSA-87-sigver-62-30 |
| ML-DSA-87-sigver-63-30 |
| ML-DSA-87-sigver-64-30 |
| ML-DSA-87-sigver-65-30 |
| ML-DSA-87-sigver-66-30 |
| ML-DSA-87-sigver-67-30 |
| ML-DSA-87-sigver-68-30 |
| ML-DSA-87-sigver-69-30 |
| ML-DSA-87-sigver-70-30 |
| ML-DSA-87-sigver-71-30 |
| ML-DSA-87-sigver-72-30 |
| ML-DSA-87-sigver-73-30 |
| ML-DSA-87-sigver-74-30 |
| ML-DSA-87-sigver-75-30 |
| ML-DSA-87-sigver-151-30 |
| ML-DSA-87-sigver-152-30 |
| ML-DSA-87-sigver-153-30 |
| ML-DSA-87-sigver-154-30 |
| ML-DSA-87-sigver-155-30 |
| ML-DSA-87-sigver-156-30 |
| ML-DSA-87-sigver-157-30 |
| ML-DSA-87-sigver-158-30 |
| ML-DSA-87-sigver-159-30 |
| ML-DSA-87-sigver-160-30 |
| ML-DSA-87-sigver-161-30 |
| ML-DSA-87-sigver-162-30 |
| ML-DSA-87-sigver-163-30 |
| ML-DSA-87-sigver-164-30 |
| ML-DSA-87-sigver-165-30 |
| ML-DSA-87-sigver-166-30 |
| ML-DSA-87-sigver-167-30 |
| ML-DSA-87-sigver-168-30 |
| ML-DSA-87-sigver-169-30 |
| ML-DSA-87-sigver-170-30 |
| ML-DSA-87-sigver-171-30 |
| ML-DSA-87-sigver-172-30 |
| ML-DSA-87-sigver-173-30 |
| ML-DSA-87-sigver-174-30 |
| ML-DSA-87-sigver-175-30 |
| ML-DSA-87-sigver-176-30 |
| ML-DSA-87-sigver-177-30 |
| ML-DSA-87-sigver-178-30 |
| ML-DSA-87-sigver-179-30 |
| ML-DSA-87-sigver-180-30 |
| ML-KEM-512-decapsulation-76-30 |
| ML-KEM-512-decapsulation-77-30 |
| ML-KEM-512-decapsulation-78-30 |
| ML-KEM-512-decapsulation-79-30 |
| ML-KEM-512-decapsulation-80-30 |
| ML-KEM-512-decapsulation-81-30 |
| ML-KEM-512-decapsulation-82-30 |
| ML-KEM-512-decapsulation-83-30 |
| ML-KEM-512-decapsulation-84-30 |
| ML-KEM-512-decapsulation-85-30 |
| ML-KEM-512-encapsulation-1-30 |
| ML-KEM-512-encapsulation-2-30 |
| ML-KEM-512-encapsulation-3-30 |
| ML-KEM-512-encapsulation-4-30 |
| ML-KEM-512-encapsulation-5-30 |
| ML-KEM-512-encapsulation-6-30 |
| ML-KEM-512-encapsulation-7-30 |
| ML-KEM-512-encapsulation-8-30 |
| ML-KEM-512-encapsulation-9-30 |
| ML-KEM-512-encapsulation-10-30 |
| ML-KEM-512-encapsulation-11-30 |
| ML-KEM-512-encapsulation-12-30 |
| ML-KEM-512-encapsulation-13-30 |
| ML-KEM-512-encapsulation-14-30 |
| ML-KEM-512-encapsulation-15-30 |
| ML-KEM-512-encapsulation-16-30 |
| ML-KEM-512-encapsulation-17-30 |
| ML-KEM-512-encapsulation-18-30 |
| ML-KEM-512-encapsulation-19-30 |
| ML-KEM-512-encapsulation-20-30 |
| ML-KEM-512-encapsulation-21-30 |
| ML-KEM-512-encapsulation-22-30 |
| ML-KEM-512-encapsulation-23-30 |
| ML-KEM-512-encapsulation-24-30 |
| ML-KEM-512-encapsulation-25-30 |
| ML-KEM-512-keygen-1-30 |
| ML-KEM-512-keygen-2-30 |
| ML-KEM-512-keygen-3-30 |
| ML-KEM-512-keygen-4-30 |
| ML-KEM-512-keygen-5-30 |
| ML-KEM-512-keygen-6-30 |
| ML-KEM-512-keygen-7-30 |
| ML-KEM-512-keygen-8-30 |
| ML-KEM-512-keygen-9-30 |
| ML-KEM-512-keygen-10-30 |
| ML-KEM-512-keygen-11-30 |
| ML-KEM-512-keygen-12-30 |
| ML-KEM-512-keygen-13-30 |
| ML-KEM-512-keygen-14-30 |
| ML-KEM-512-keygen-15-30 |
| ML-KEM-512-keygen-16-30 |
| ML-KEM-512-keygen-17-30 |
| ML-KEM-512-keygen-18-30 |
| ML-KEM-512-keygen-19-30 |
| ML-KEM-512-keygen-20-30 |
| ML-KEM-512-keygen-21-30 |
| ML-KEM-512-keygen-22-30 |
| ML-KEM-512-keygen-23-30 |
| ML-KEM-512-keygen-24-30 |
| ML-KEM-512-keygen-25-30 |
| ML-KEM-768-decapsulation-86-30 |
| ML-KEM-768-decapsulation-87-30 |
| ML-KEM-768-decapsulation-88-30 |
| ML-KEM-768-decapsulation-89-30 |
| ML-KEM-768-decapsulation-90-30 |
| ML-KEM-768-decapsulation-91-30 |
| ML-KEM-768-decapsulation-92-30 |
| ML-KEM-768-decapsulation-93-30 |
| ML-KEM-768-decapsulation-94-30 |
| ML-KEM-768-decapsulation-95-30 |
| ML-KEM-768-encapsulation-26-30 |
| ML-KEM-768-encapsulation-27-30 |
| ML-KEM-768-encapsulation-28-30 |
| ML-KEM-768-encapsulation-29-30 |
| ML-KEM-768-encapsulation-30-30 |
| ML-KEM-768-encapsulation-31-30 |
| ML-KEM-768-encapsulation-32-30 |
| ML-KEM-768-encapsulation-33-30 |
| ML-KEM-768-encapsulation-34-30 |
| ML-KEM-768-encapsulation-35-30 |
| ML-KEM-768-encapsulation-36-30 |
| ML-KEM-768-encapsulation-37-30 |
| ML-KEM-768-encapsulation-38-30 |
| ML-KEM-768-encapsulation-39-30 |
| ML-KEM-768-encapsulation-40-30 |
| ML-KEM-768-encapsulation-41-30 |
| ML-KEM-768-encapsulation-42-30 |
| ML-KEM-768-encapsulation-43-30 |
| ML-KEM-768-encapsulation-44-30 |
| ML-KEM-768-encapsulation-45-30 |
| ML-KEM-768-encapsulation-46-30 |
| ML-KEM-768-encapsulation-47-30 |
| ML-KEM-768-encapsulation-48-30 |
| ML-KEM-768-encapsulation-49-30 |
| ML-KEM-768-encapsulation-50-30 |
| ML-KEM-768-keygen-26-30 |
| ML-KEM-768-keygen-27-30 |
| ML-KEM-768-keygen-28-30 |
| ML-KEM-768-keygen-29-30 |
| ML-KEM-768-keygen-30-30 |
| ML-KEM-768-keygen-31-30 |
| ML-KEM-768-keygen-32-30 |
| ML-KEM-768-keygen-33-30 |
| ML-KEM-768-keygen-34-30 |
| ML-KEM-768-keygen-35-30 |
| ML-KEM-768-keygen-36-30 |
| ML-KEM-768-keygen-37-30 |
| ML-KEM-768-keygen-38-30 |
| ML-KEM-768-keygen-39-30 |
| ML-KEM-768-keygen-40-30 |
| ML-KEM-768-keygen-41-30 |
| ML-KEM-768-keygen-42-30 |
| ML-KEM-768-keygen-43-30 |
| ML-KEM-768-keygen-44-30 |
| ML-KEM-768-keygen-45-30 |
| ML-KEM-768-keygen-46-30 |
| ML-KEM-768-keygen-47-30 |
| ML-KEM-768-keygen-48-30 |
| ML-KEM-768-keygen-49-30 |
| ML-KEM-768-keygen-50-30 |
| ML-KEM-1024-decapsulation-96-30 |
| ML-KEM-1024-decapsulation-97-30 |
| ML-KEM-1024-decapsulation-98-30 |
| ML-KEM-1024-decapsulation-99-30 |
| ML-KEM-1024-decapsulation-100-30 |
| ML-KEM-1024-decapsulation-101-30 |
| ML-KEM-1024-decapsulation-102-30 |
| ML-KEM-1024-decapsulation-103-30 |
| ML-KEM-1024-decapsulation-104-30 |
| ML-KEM-1024-decapsulation-105-30 |
| ML-KEM-1024-encapsulation-51-30 |
| ML-KEM-1024-encapsulation-52-30 |
| ML-KEM-1024-encapsulation-53-30 |
| ML-KEM-1024-encapsulation-54-30 |
| ML-KEM-1024-encapsulation-55-30 |
| ML-KEM-1024-encapsulation-56-30 |
| ML-KEM-1024-encapsulation-57-30 |
| ML-KEM-1024-encapsulation-58-30 |
| ML-KEM-1024-encapsulation-59-30 |
| ML-KEM-1024-encapsulation-60-30 |
| ML-KEM-1024-encapsulation-61-30 |
| ML-KEM-1024-encapsulation-62-30 |
| ML-KEM-1024-encapsulation-63-30 |
| ML-KEM-1024-encapsulation-64-30 |
| ML-KEM-1024-encapsulation-65-30 |
| ML-KEM-1024-encapsulation-66-30 |
| ML-KEM-1024-encapsulation-67-30 |
| ML-KEM-1024-encapsulation-68-30 |
| ML-KEM-1024-encapsulation-69-30 |
| ML-KEM-1024-encapsulation-70-30 |
| ML-KEM-1024-encapsulation-71-30 |
| ML-KEM-1024-encapsulation-72-30 |
| ML-KEM-1024-encapsulation-73-30 |
| ML-KEM-1024-encapsulation-74-30 |
| ML-KEM-1024-encapsulation-75-30 |
| ML-KEM-1024-keygen-51-30 |
| ML-KEM-1024-keygen-52-30 |
| ML-KEM-1024-keygen-53-30 |
| ML-KEM-1024-keygen-54-30 |
| ML-KEM-1024-keygen-55-30 |
| ML-KEM-1024-keygen-56-30 |
| ML-KEM-1024-keygen-57-30 |
| ML-KEM-1024-keygen-58-30 |
| ML-KEM-1024-keygen-59-30 |
| ML-KEM-1024-keygen-60-30 |
| ML-KEM-1024-keygen-61-30 |
| ML-KEM-1024-keygen-62-30 |
| ML-KEM-1024-keygen-63-30 |
| ML-KEM-1024-keygen-64-30 |
| ML-KEM-1024-keygen-65-30 |
| ML-KEM-1024-keygen-66-30 |
| ML-KEM-1024-keygen-67-30 |
| ML-KEM-1024-keygen-68-30 |
| ML-KEM-1024-keygen-69-30 |
| ML-KEM-1024-keygen-70-30 |
| ML-KEM-1024-keygen-71-30 |
| ML-KEM-1024-keygen-72-30 |
| ML-KEM-1024-keygen-73-30 |
| ML-KEM-1024-keygen-74-30 |
| ML-KEM-1024-keygen-75-30 |
| SLH-DSA-SHA2-128f-keygen-21-30 |
| SLH-DSA-SHA2-128f-keygen-22-30 |
| SLH-DSA-SHA2-128f-keygen-23-30 |
| SLH-DSA-SHA2-128f-keygen-24-30 |
| SLH-DSA-SHA2-128f-keygen-25-30 |
| SLH-DSA-SHA2-128f-keygen-26-30 |
| SLH-DSA-SHA2-128f-keygen-27-30 |
| SLH-DSA-SHA2-128f-keygen-28-30 |
| SLH-DSA-SHA2-128f-keygen-29-30 |
| SLH-DSA-SHA2-128f-keygen-30-30 |
| SLH-DSA-SHA2-128f-siggen-1-30 |
| SLH-DSA-SHA2-128f-siggen-2-30 |
| SLH-DSA-SHA2-128f-siggen-3-30 |
| SLH-DSA-SHA2-128f-siggen-4-30 |
| SLH-DSA-SHA2-128f-siggen-5-30 |
| SLH-DSA-SHA2-128f-siggen-6-30 |
| SLH-DSA-SHA2-128f-siggen-7-30 |
| SLH-DSA-SHA2-128f-siggen-115-30 |
| SLH-DSA-SHA2-128f-siggen-116-30 |
| SLH-DSA-SHA2-128f-siggen-117-30 |
| SLH-DSA-SHA2-128f-siggen-118-30 |
| SLH-DSA-SHA2-128f-siggen-119-30 |
| SLH-DSA-SHA2-128f-siggen-120-30 |
| SLH-DSA-SHA2-128f-siggen-121-30 |
| SLH-DSA-SHA2-128f-siggen-313-30 |
| SLH-DSA-SHA2-128f-siggen-314-30 |
| SLH-DSA-SHA2-128f-siggen-315-30 |
| SLH-DSA-SHA2-128f-siggen-316-30 |
| SLH-DSA-SHA2-128f-siggen-317-30 |
| SLH-DSA-SHA2-128f-siggen-318-30 |
| SLH-DSA-SHA2-128f-siggen-319-30 |
| SLH-DSA-SHA2-128f-siggen-427-30 |
| SLH-DSA-SHA2-128f-siggen-428-30 |
| SLH-DSA-SHA2-128f-siggen-429-30 |
| SLH-DSA-SHA2-128f-siggen-430-30 |
| SLH-DSA-SHA2-128f-siggen-431-30 |
| SLH-DSA-SHA2-128f-siggen-432-30 |
| SLH-DSA-SHA2-128f-siggen-433-30 |
| SLH-DSA-SHA2-128f-sigver-1-30 |
| SLH-DSA-SHA2-128f-sigver-2-30 |
| SLH-DSA-SHA2-128f-sigver-3-30 |
| SLH-DSA-SHA2-128f-sigver-4-30 |
| SLH-DSA-SHA2-128f-sigver-5-30 |
| SLH-DSA-SHA2-128f-sigver-6-30 |
| SLH-DSA-SHA2-128f-sigver-7-30 |
| SLH-DSA-SHA2-128f-sigver-8-30 |
| SLH-DSA-SHA2-128f-sigver-9-30 |
| SLH-DSA-SHA2-128f-sigver-10-30 |
| SLH-DSA-SHA2-128f-sigver-11-30 |
| SLH-DSA-SHA2-128f-sigver-12-30 |
| SLH-DSA-SHA2-128f-sigver-13-30 |
| SLH-DSA-SHA2-128f-sigver-14-30 |
| SLH-DSA-SHA2-128f-sigver-169-30 |
| SLH-DSA-SHA2-128f-sigver-170-30 |
| SLH-DSA-SHA2-128f-sigver-171-30 |
| SLH-DSA-SHA2-128f-sigver-172-30 |
| SLH-DSA-SHA2-128f-sigver-173-30 |
| SLH-DSA-SHA2-128f-sigver-174-30 |
| SLH-DSA-SHA2-128f-sigver-175-30 |
| SLH-DSA-SHA2-128f-sigver-176-30 |
| SLH-DSA-SHA2-128f-sigver-177-30 |
| SLH-DSA-SHA2-128f-sigver-178-30 |
| SLH-DSA-SHA2-128f-sigver-179-30 |
| SLH-DSA-SHA2-128f-sigver-180-30 |
| SLH-DSA-SHA2-128f-sigver-181-30 |
| SLH-DSA-SHA2-128f-sigver-182-30 |
| SLH-DSA-SHA2-128s-keygen-1-30 |
| SLH-DSA-SHA2-128s-keygen-2-30 |
| SLH-DSA-SHA2-128s-keygen-3-30 |
| SLH-DSA-SHA2-128s-keygen-4-30 |
| SLH-DSA-SHA2-128s-keygen-5-30 |
| SLH-DSA-SHA2-128s-keygen-6-30 |
| SLH-DSA-SHA2-128s-keygen-7-30 |
| SLH-DSA-SHA2-128s-keygen-8-30 |
| SLH-DSA-SHA2-128s-keygen-9-30 |
| SLH-DSA-SHA2-128s-keygen-10-30 |
| SLH-DSA-SHA2-128s-siggen-157-30 |
| SLH-DSA-SHA2-128s-siggen-158-30 |
| SLH-DSA-SHA2-128s-siggen-159-30 |
| SLH-DSA-SHA2-128s-siggen-160-30 |
| SLH-DSA-SHA2-128s-siggen-161-30 |
| SLH-DSA-SHA2-128s-siggen-162-30 |
| SLH-DSA-SHA2-128s-siggen-163-30 |
| SLH-DSA-SHA2-128s-siggen-271-30 |
| SLH-DSA-SHA2-128s-siggen-272-30 |
| SLH-DSA-SHA2-128s-siggen-273-30 |
| SLH-DSA-SHA2-128s-siggen-274-30 |
| SLH-DSA-SHA2-128s-siggen-275-30 |
| SLH-DSA-SHA2-128s-siggen-276-30 |
| SLH-DSA-SHA2-128s-siggen-277-30 |
| SLH-DSA-SHA2-128s-siggen-469-30 |
| SLH-DSA-SHA2-128s-siggen-470-30 |
| SLH-DSA-SHA2-128s-siggen-471-30 |
| SLH-DSA-SHA2-128s-siggen-472-30 |
| SLH-DSA-SHA2-128s-siggen-473-30 |
| SLH-DSA-SHA2-128s-siggen-474-30 |
| SLH-DSA-SHA2-128s-siggen-475-30 |
| SLH-DSA-SHA2-128s-siggen-583-30 |
| SLH-DSA-SHA2-128s-siggen-584-30 |
| SLH-DSA-SHA2-128s-siggen-585-30 |
| SLH-DSA-SHA2-128s-siggen-586-30 |
| SLH-DSA-SHA2-128s-siggen-587-30 |
| SLH-DSA-SHA2-128s-siggen-588-30 |
| SLH-DSA-SHA2-128s-siggen-589-30 |
| SLH-DSA-SHA2-128s-sigver-253-30 |
| SLH-DSA-SHA2-128s-sigver-254-30 |
| SLH-DSA-SHA2-128s-sigver-255-30 |
| SLH-DSA-SHA2-128s-sigver-256-30 |
| SLH-DSA-SHA2-128s-sigver-257-30 |
| SLH-DSA-SHA2-128s-sigver-258-30 |
| SLH-DSA-SHA2-128s-sigver-259-30 |
| SLH-DSA-SHA2-128s-sigver-260-30 |
| SLH-DSA-SHA2-128s-sigver-261-30 |
| SLH-DSA-SHA2-128s-sigver-262-30 |
| SLH-DSA-SHA2-128s-sigver-263-30 |
| SLH-DSA-SHA2-128s-sigver-264-30 |
| SLH-DSA-SHA2-128s-sigver-265-30 |
| SLH-DSA-SHA2-128s-sigver-266-30 |
| SLH-DSA-SHA2-128s-sigver-421-30 |
| SLH-DSA-SHA2-128s-sigver-422-30 |
| SLH-DSA-SHA2-128s-sigver-423-30 |
| SLH-DSA-SHA2-128s-sigver-424-30 |
| SLH-DSA-SHA2-128s-sigver-425-30 |
| SLH-DSA-SHA2-128s-sigver-426-30 |
| SLH-DSA-SHA2-128s-sigver-427-30 |
| SLH-DSA-SHA2-128s-sigver-428-30 |
| SLH-DSA-SHA2-128s-sigver-429-30 |
| SLH-DSA-SHA2-128s-sigver-430-30 |
| SLH-DSA-SHA2-128s-sigver-431-30 |
| SLH-DSA-SHA2-128s-sigver-432-30 |
| SLH-DSA-SHA2-128s-sigver-433-30 |
| SLH-DSA-SHA2-128s-sigver-434-30 |
| SLH-DSA-SHA2-192f-keygen-61-30 |
| SLH-DSA-SHA2-192f-keygen-62-30 |
| SLH-DSA-SHA2-192f-keygen-63-30 |
| SLH-DSA-SHA2-192f-keygen-64-30 |
| SLH-DSA-SHA2-192f-keygen-65-30 |
| SLH-DSA-SHA2-192f-keygen-66-30 |
| SLH-DSA-SHA2-192f-keygen-67-30 |
| SLH-DSA-SHA2-192f-keygen-68-30 |
| SLH-DSA-SHA2-192f-keygen-69-30 |
| SLH-DSA-SHA2-192f-keygen-70-30 |
| SLH-DSA-SHA2-192f-siggen-20-30 |
| SLH-DSA-SHA2-192f-siggen-21-30 |
| SLH-DSA-SHA2-192f-siggen-22-30 |
| SLH-DSA-SHA2-192f-siggen-23-30 |
| SLH-DSA-SHA2-192f-siggen-24-30 |
| SLH-DSA-SHA2-192f-siggen-25-30 |
| SLH-DSA-SHA2-192f-siggen-26-30 |
| SLH-DSA-SHA2-192f-siggen-122-30 |
| SLH-DSA-SHA2-192f-siggen-123-30 |
| SLH-DSA-SHA2-192f-siggen-124-30 |
| SLH-DSA-SHA2-192f-siggen-125-30 |
| SLH-DSA-SHA2-192f-siggen-126-30 |
| SLH-DSA-SHA2-192f-siggen-127-30 |
| SLH-DSA-SHA2-192f-siggen-128-30 |
| SLH-DSA-SHA2-192f-siggen-332-30 |
| SLH-DSA-SHA2-192f-siggen-333-30 |
| SLH-DSA-SHA2-192f-siggen-334-30 |
| SLH-DSA-SHA2-192f-siggen-335-30 |
| SLH-DSA-SHA2-192f-siggen-336-30 |
| SLH-DSA-SHA2-192f-siggen-337-30 |
| SLH-DSA-SHA2-192f-siggen-338-30 |
| SLH-DSA-SHA2-192f-siggen-434-30 |
| SLH-DSA-SHA2-192f-siggen-435-30 |
| SLH-DSA-SHA2-192f-siggen-436-30 |
| SLH-DSA-SHA2-192f-siggen-437-30 |
| SLH-DSA-SHA2-192f-siggen-438-30 |
| SLH-DSA-SHA2-192f-siggen-439-30 |
| SLH-DSA-SHA2-192f-siggen-440-30 |
| SLH-DSA-SHA2-192f-sigver-29-30 |
| SLH-DSA-SHA2-192f-sigver-30-30 |
| SLH-DSA-SHA2-192f-sigver-31-30 |
| SLH-DSA-SHA2-192f-sigver-32-30 |
| SLH-DSA-SHA2-192f-sigver-33-30 |
| SLH-DSA-SHA2-192f-sigver-34-30 |
| SLH-DSA-SHA2-192f-sigver-35-30 |
| SLH-DSA-SHA2-192f-sigver-36-30 |
| SLH-DSA-SHA2-192f-sigver-37-30 |
| SLH-DSA-SHA2-192f-sigver-38-30 |
| SLH-DSA-SHA2-192f-sigver-39-30 |
| SLH-DSA-SHA2-192f-sigver-40-30 |
| SLH-DSA-SHA2-192f-sigver-41-30 |
| SLH-DSA-SHA2-192f-sigver-42-30 |
| SLH-DSA-SHA2-192f-sigver-183-30 |
| SLH-DSA-SHA2-192f-sigver-184-30 |
| SLH-DSA-SHA2-192f-sigver-185-30 |
| SLH-DSA-SHA2-192f-sigver-186-30 |
| SLH-DSA-SHA2-192f-sigver-187-30 |
| SLH-DSA-SHA2-192f-sigver-188-30 |
| SLH-DSA-SHA2-192f-sigver-189-30 |
| SLH-DSA-SHA2-192f-sigver-190-30 |
| SLH-DSA-SHA2-192f-sigver-191-30 |
| SLH-DSA-SHA2-192f-sigver-192-30 |
| SLH-DSA-SHA2-192f-sigver-193-30 |
| SLH-DSA-SHA2-192f-sigver-194-30 |
| SLH-DSA-SHA2-192f-sigver-195-30 |
| SLH-DSA-SHA2-192f-sigver-196-30 |
| SLH-DSA-SHA2-192s-keygen-41-30 |
| SLH-DSA-SHA2-192s-keygen-42-30 |
| SLH-DSA-SHA2-192s-keygen-43-30 |
| SLH-DSA-SHA2-192s-keygen-44-30 |
| SLH-DSA-SHA2-192s-keygen-45-30 |
| SLH-DSA-SHA2-192s-keygen-46-30 |
| SLH-DSA-SHA2-192s-keygen-47-30 |
| SLH-DSA-SHA2-192s-keygen-48-30 |
| SLH-DSA-SHA2-192s-keygen-49-30 |
| SLH-DSA-SHA2-192s-keygen-50-30 |
| SLH-DSA-SHA2-192s-siggen-176-30 |
| SLH-DSA-SHA2-192s-siggen-177-30 |
| SLH-DSA-SHA2-192s-siggen-178-30 |
| SLH-DSA-SHA2-192s-siggen-179-30 |
| SLH-DSA-SHA2-192s-siggen-180-30 |
| SLH-DSA-SHA2-192s-siggen-181-30 |
| SLH-DSA-SHA2-192s-siggen-182-30 |
| SLH-DSA-SHA2-192s-siggen-278-30 |
| SLH-DSA-SHA2-192s-siggen-279-30 |
| SLH-DSA-SHA2-192s-siggen-280-30 |
| SLH-DSA-SHA2-192s-siggen-281-30 |
| SLH-DSA-SHA2-192s-siggen-282-30 |
| SLH-DSA-SHA2-192s-siggen-283-30 |
| SLH-DSA-SHA2-192s-siggen-284-30 |
| SLH-DSA-SHA2-192s-siggen-488-30 |
| SLH-DSA-SHA2-192s-siggen-489-30 |
| SLH-DSA-SHA2-192s-siggen-490-30 |
| SLH-DSA-SHA2-192s-siggen-491-30 |
| SLH-DSA-SHA2-192s-siggen-492-30 |
| SLH-DSA-SHA2-192s-siggen-493-30 |
| SLH-DSA-SHA2-192s-siggen-494-30 |
| SLH-DSA-SHA2-192s-siggen-590-30 |
| SLH-DSA-SHA2-192s-siggen-591-30 |
| SLH-DSA-SHA2-192s-siggen-592-30 |
| SLH-DSA-SHA2-192s-siggen-593-30 |
| SLH-DSA-SHA2-192s-siggen-594-30 |
| SLH-DSA-SHA2-192s-siggen-595-30 |
| SLH-DSA-SHA2-192s-siggen-596-30 |
| SLH-DSA-SHA2-192s-sigver-281-30 |
| SLH-DSA-SHA2-192s-sigver-282-30 |
| SLH-DSA-SHA2-192s-sigver-283-30 |
| SLH-DSA-SHA2-192s-sigver-284-30 |
| SLH-DSA-SHA2-192s-sigver-285-30 |
| SLH-DSA-SHA2-192s-sigver-286-30 |
| SLH-DSA-SHA2-192s-sigver-287-30 |
| SLH-DSA-SHA2-192s-sigver-288-30 |
| SLH-DSA-SHA2-192s-sigver-289-30 |
| SLH-DSA-SHA2-192s-sigver-290-30 |
| SLH-DSA-SHA2-192s-sigver-291-30 |
| SLH-DSA-SHA2-192s-sigver-292-30 |
| SLH-DSA-SHA2-192s-sigver-293-30 |
| SLH-DSA-SHA2-192s-sigver-294-30 |
| SLH-DSA-SHA2-192s-sigver-435-30 |
| SLH-DSA-SHA2-192s-sigver-436-30 |
| SLH-DSA-SHA2-192s-sigver-437-30 |
| SLH-DSA-SHA2-192s-sigver-438-30 |
| SLH-DSA-SHA2-192s-sigver-439-30 |
| SLH-DSA-SHA2-192s-sigver-440-30 |
| SLH-DSA-SHA2-192s-sigver-441-30 |
| SLH-DSA-SHA2-192s-sigver-442-30 |
| SLH-DSA-SHA2-192s-sigver-443-30 |
| SLH-DSA-SHA2-192s-sigver-444-30 |
| SLH-DSA-SHA2-192s-sigver-445-30 |
| SLH-DSA-SHA2-192s-sigver-446-30 |
| SLH-DSA-SHA2-192s-sigver-447-30 |
| SLH-DSA-SHA2-192s-sigver-448-30 |
| SLH-DSA-SHA2-256f-keygen-101-30 |
| SLH-DSA-SHA2-256f-keygen-102-30 |
| SLH-DSA-SHA2-256f-keygen-103-30 |
| SLH-DSA-SHA2-256f-keygen-104-30 |
| SLH-DSA-SHA2-256f-keygen-105-30 |
| SLH-DSA-SHA2-256f-keygen-106-30 |
| SLH-DSA-SHA2-256f-keygen-107-30 |
| SLH-DSA-SHA2-256f-keygen-108-30 |
| SLH-DSA-SHA2-256f-keygen-109-30 |
| SLH-DSA-SHA2-256f-keygen-110-30 |
| SLH-DSA-SHA2-256f-siggen-39-30 |
| SLH-DSA-SHA2-256f-siggen-40-30 |
| SLH-DSA-SHA2-256f-siggen-41-30 |
| SLH-DSA-SHA2-256f-siggen-42-30 |
| SLH-DSA-SHA2-256f-siggen-43-30 |
| SLH-DSA-SHA2-256f-siggen-44-30 |
| SLH-DSA-SHA2-256f-siggen-45-30 |
| SLH-DSA-SHA2-256f-siggen-129-30 |
| SLH-DSA-SHA2-256f-siggen-130-30 |
| SLH-DSA-SHA2-256f-siggen-131-30 |
| SLH-DSA-SHA2-256f-siggen-132-30 |
| SLH-DSA-SHA2-256f-siggen-133-30 |
| SLH-DSA-SHA2-256f-siggen-134-30 |
| SLH-DSA-SHA2-256f-siggen-135-30 |
| SLH-DSA-SHA2-256f-siggen-351-30 |
| SLH-DSA-SHA2-256f-siggen-352-30 |
| SLH-DSA-SHA2-256f-siggen-353-30 |
| SLH-DSA-SHA2-256f-siggen-354-30 |
| SLH-DSA-SHA2-256f-siggen-355-30 |
| SLH-DSA-SHA2-256f-siggen-356-30 |
| SLH-DSA-SHA2-256f-siggen-357-30 |
| SLH-DSA-SHA2-256f-siggen-441-30 |
| SLH-DSA-SHA2-256f-siggen-442-30 |
| SLH-DSA-SHA2-256f-siggen-443-30 |
| SLH-DSA-SHA2-256f-siggen-444-30 |
| SLH-DSA-SHA2-256f-siggen-445-30 |
| SLH-DSA-SHA2-256f-siggen-446-30 |
| SLH-DSA-SHA2-256f-siggen-447-30 |
| SLH-DSA-SHA2-256f-sigver-57-30 |
| SLH-DSA-SHA2-256f-sigver-58-30 |
| SLH-DSA-SHA2-256f-sigver-59-30 |
| SLH-DSA-SHA2-256f-sigver-60-30 |
| SLH-DSA-SHA2-256f-sigver-61-30 |
| SLH-DSA-SHA2-256f-sigver-62-30 |
| SLH-DSA-SHA2-256f-sigver-63-30 |
| SLH-DSA-SHA2-256f-sigver-64-301 |
| SLH-DSA-SHA2-256f-sigver-65-301 |
| SLH-DSA-SHA2-256f-sigver-66-301 |
| SLH-DSA-SHA2-256f-sigver-67-301 |
| SLH-DSA-SHA2-256f-sigver-68-301 |
| SLH-DSA-SHA2-256f-sigver-69-30 |
| SLH-DSA-SHA2-256f-sigver-70-30 |
| SLH-DSA-SHA2-256f-sigver-197-30 |
| SLH-DSA-SHA2-256f-sigver-198-30 |
| SLH-DSA-SHA2-256f-sigver-199-30 |
| SLH-DSA-SHA2-256f-sigver-200-30 |
| SLH-DSA-SHA2-256f-sigver-201-30 |
| SLH-DSA-SHA2-256f-sigver-202-30 |
| SLH-DSA-SHA2-256f-sigver-203-30 |
| SLH-DSA-SHA2-256f-sigver-204-30 |
| SLH-DSA-SHA2-256f-sigver-205-30 |
| SLH-DSA-SHA2-256f-sigver-206-30 |
| SLH-DSA-SHA2-256f-sigver-207-30 |
| SLH-DSA-SHA2-256f-sigver-208-30 |
| SLH-DSA-SHA2-256f-sigver-209-30 |
| SLH-DSA-SHA2-256f-sigver-210-30 |
| SLH-DSA-SHA2-256s-keygen-81-30 |
| SLH-DSA-SHA2-256s-keygen-82-30 |
| SLH-DSA-SHA2-256s-keygen-83-30 |
| SLH-DSA-SHA2-256s-keygen-84-30 |
| SLH-DSA-SHA2-256s-keygen-85-30 |
| SLH-DSA-SHA2-256s-keygen-86-30 |
| SLH-DSA-SHA2-256s-keygen-87-30 |
| SLH-DSA-SHA2-256s-keygen-88-30 |
| SLH-DSA-SHA2-256s-keygen-89-30 |
| SLH-DSA-SHA2-256s-keygen-90-30 |
| SLH-DSA-SHA2-256s-siggen-195-30 |
| SLH-DSA-SHA2-256s-siggen-196-30 |
| SLH-DSA-SHA2-256s-siggen-197-30 |
| SLH-DSA-SHA2-256s-siggen-198-30 |
| SLH-DSA-SHA2-256s-siggen-199-30 |
| SLH-DSA-SHA2-256s-siggen-200-30 |
| SLH-DSA-SHA2-256s-siggen-201-30 |
| SLH-DSA-SHA2-256s-siggen-285-30 |
| SLH-DSA-SHA2-256s-siggen-286-30 |
| SLH-DSA-SHA2-256s-siggen-287-30 |
| SLH-DSA-SHA2-256s-siggen-288-30 |
| SLH-DSA-SHA2-256s-siggen-289-30 |
| SLH-DSA-SHA2-256s-siggen-290-30 |
| SLH-DSA-SHA2-256s-siggen-291-30 |
| SLH-DSA-SHA2-256s-siggen-507-30 |
| SLH-DSA-SHA2-256s-siggen-508-30 |
| SLH-DSA-SHA2-256s-siggen-509-30 |
| SLH-DSA-SHA2-256s-siggen-510-30 |
| SLH-DSA-SHA2-256s-siggen-511-30 |
| SLH-DSA-SHA2-256s-siggen-512-30 |
| SLH-DSA-SHA2-256s-siggen-513-30 |
| SLH-DSA-SHA2-256s-siggen-597-30 |
| SLH-DSA-SHA2-256s-siggen-598-30 |
| SLH-DSA-SHA2-256s-siggen-599-30 |
| SLH-DSA-SHA2-256s-siggen-600-30 |
| SLH-DSA-SHA2-256s-siggen-601-30 |
| SLH-DSA-SHA2-256s-siggen-602-30 |
| SLH-DSA-SHA2-256s-siggen-603-30 |
| SLH-DSA-SHA2-256s-sigver-309-30 |
| SLH-DSA-SHA2-256s-sigver-310-30 |
| SLH-DSA-SHA2-256s-sigver-311-30 |
| SLH-DSA-SHA2-256s-sigver-312-30 |
| SLH-DSA-SHA2-256s-sigver-313-30 |
| SLH-DSA-SHA2-256s-sigver-314-30 |
| SLH-DSA-SHA2-256s-sigver-315-30 |
| SLH-DSA-SHA2-256s-sigver-316-30 |
| SLH-DSA-SHA2-256s-sigver-317-30 |
| SLH-DSA-SHA2-256s-sigver-318-30 |
| SLH-DSA-SHA2-256s-sigver-319-30 |
| SLH-DSA-SHA2-256s-sigver-320-30 |
| SLH-DSA-SHA2-256s-sigver-321-30 |
| SLH-DSA-SHA2-256s-sigver-322-30 |
| SLH-DSA-SHA2-256s-sigver-449-30 |
| SLH-DSA-SHA2-256s-sigver-450-30 |
| SLH-DSA-SHA2-256s-sigver-451-30 |
| SLH-DSA-SHA2-256s-sigver-452-30 |
| SLH-DSA-SHA2-256s-sigver-453-30 |
| SLH-DSA-SHA2-256s-sigver-454-30 |
| SLH-DSA-SHA2-256s-sigver-455-30 |
| SLH-DSA-SHA2-256s-sigver-456-30 |
| SLH-DSA-SHA2-256s-sigver-457-30 |
| SLH-DSA-SHA2-256s-sigver-458-30 |
| SLH-DSA-SHA2-256s-sigver-459-30 |
| SLH-DSA-SHA2-256s-sigver-460-30 |
| SLH-DSA-SHA2-256s-sigver-461-30 |
| SLH-DSA-SHA2-256s-sigver-462-30 |
| SLH-DSA-SHAKE-128f-keygen-31-30 |
| SLH-DSA-SHAKE-128f-keygen-32-30 |
| SLH-DSA-SHAKE-128f-keygen-33-30 |
| SLH-DSA-SHAKE-128f-keygen-34-30 |
| SLH-DSA-SHAKE-128f-keygen-35-30 |
| SLH-DSA-SHAKE-128f-keygen-36-30 |
| SLH-DSA-SHAKE-128f-keygen-37-30 |
| SLH-DSA-SHAKE-128f-keygen-38-30 |
| SLH-DSA-SHAKE-128f-keygen-39-30 |
| SLH-DSA-SHAKE-128f-keygen-40-30 |
| SLH-DSA-SHAKE-128f-siggen-58-30 |
| SLH-DSA-SHAKE-128f-siggen-59-30 |
| SLH-DSA-SHAKE-128f-siggen-60-30 |
| SLH-DSA-SHAKE-128f-siggen-61-30 |
| SLH-DSA-SHAKE-128f-siggen-62-30 |
| SLH-DSA-SHAKE-128f-siggen-63-30 |
| SLH-DSA-SHAKE-128f-siggen-64-30 |
| SLH-DSA-SHAKE-128f-siggen-136-30 |
| SLH-DSA-SHAKE-128f-siggen-137-30 |
| SLH-DSA-SHAKE-128f-siggen-138-30 |
| SLH-DSA-SHAKE-128f-siggen-139-30 |
| SLH-DSA-SHAKE-128f-siggen-140-30 |
| SLH-DSA-SHAKE-128f-siggen-141-30 |
| SLH-DSA-SHAKE-128f-siggen-142-30 |
| SLH-DSA-SHAKE-128f-siggen-370-30 |
| SLH-DSA-SHAKE-128f-siggen-371-30 |
| SLH-DSA-SHAKE-128f-siggen-372-30 |
| SLH-DSA-SHAKE-128f-siggen-373-30 |
| SLH-DSA-SHAKE-128f-siggen-374-30 |
| SLH-DSA-SHAKE-128f-siggen-375-30 |
| SLH-DSA-SHAKE-128f-siggen-376-30 |
| SLH-DSA-SHAKE-128f-siggen-448-30 |
| SLH-DSA-SHAKE-128f-siggen-449-30 |
| SLH-DSA-SHAKE-128f-siggen-450-30 |
| SLH-DSA-SHAKE-128f-siggen-451-30 |
| SLH-DSA-SHAKE-128f-siggen-452-30 |
| SLH-DSA-SHAKE-128f-siggen-453-30 |
| SLH-DSA-SHAKE-128f-siggen-454-30 |
| SLH-DSA-SHAKE-128f-sigver-85-30 |
| SLH-DSA-SHAKE-128f-sigver-86-30 |
| SLH-DSA-SHAKE-128f-sigver-87-30 |
| SLH-DSA-SHAKE-128f-sigver-88-30 |
| SLH-DSA-SHAKE-128f-sigver-89-30 |
| SLH-DSA-SHAKE-128f-sigver-90-30 |
| SLH-DSA-SHAKE-128f-sigver-91-30 |
| SLH-DSA-SHAKE-128f-sigver-92-30 |
| SLH-DSA-SHAKE-128f-sigver-93-30 |
| SLH-DSA-SHAKE-128f-sigver-94-30 |
| SLH-DSA-SHAKE-128f-sigver-95-30 |
| SLH-DSA-SHAKE-128f-sigver-96-30 |
| SLH-DSA-SHAKE-128f-sigver-97-30 |
| SLH-DSA-SHAKE-128f-sigver-98-30 |
| SLH-DSA-SHAKE-128f-sigver-211-30 |
| SLH-DSA-SHAKE-128f-sigver-212-30 |
| SLH-DSA-SHAKE-128f-sigver-213-30 |
| SLH-DSA-SHAKE-128f-sigver-214-30 |
| SLH-DSA-SHAKE-128f-sigver-215-30 |
| SLH-DSA-SHAKE-128f-sigver-216-30 |
| SLH-DSA-SHAKE-128f-sigver-217-30 |
| SLH-DSA-SHAKE-128f-sigver-218-30 |
| SLH-DSA-SHAKE-128f-sigver-219-30 |
| SLH-DSA-SHAKE-128f-sigver-220-30 |
| SLH-DSA-SHAKE-128f-sigver-221-30 |
| SLH-DSA-SHAKE-128f-sigver-222-30 |
| SLH-DSA-SHAKE-128f-sigver-223-30 |
| SLH-DSA-SHAKE-128f-sigver-224-30 |
| SLH-DSA-SHAKE-128s-keygen-11-30 |
| SLH-DSA-SHAKE-128s-keygen-12-30 |
| SLH-DSA-SHAKE-128s-keygen-13-30 |
| SLH-DSA-SHAKE-128s-keygen-14-30 |
| SLH-DSA-SHAKE-128s-keygen-15-30 |
| SLH-DSA-SHAKE-128s-keygen-16-30 |
| SLH-DSA-SHAKE-128s-keygen-17-30 |
| SLH-DSA-SHAKE-128s-keygen-18-30 |
| SLH-DSA-SHAKE-128s-keygen-19-30 |
| SLH-DSA-SHAKE-128s-keygen-20-30 |
| SLH-DSA-SHAKE-128s-siggen-214-30 |
| SLH-DSA-SHAKE-128s-siggen-215-30 |
| SLH-DSA-SHAKE-128s-siggen-216-30 |
| SLH-DSA-SHAKE-128s-siggen-217-30 |
| SLH-DSA-SHAKE-128s-siggen-218-30 |
| SLH-DSA-SHAKE-128s-siggen-219-30 |
| SLH-DSA-SHAKE-128s-siggen-220-30 |
| SLH-DSA-SHAKE-128s-siggen-292-30 |
| SLH-DSA-SHAKE-128s-siggen-293-30 |
| SLH-DSA-SHAKE-128s-siggen-294-30 |
| SLH-DSA-SHAKE-128s-siggen-295-30 |
| SLH-DSA-SHAKE-128s-siggen-296-30 |
| SLH-DSA-SHAKE-128s-siggen-297-30 |
| SLH-DSA-SHAKE-128s-siggen-298-30 |
| SLH-DSA-SHAKE-128s-siggen-526-30 |
| SLH-DSA-SHAKE-128s-siggen-527-30 |
| SLH-DSA-SHAKE-128s-siggen-528-30 |
| SLH-DSA-SHAKE-128s-siggen-529-30 |
| SLH-DSA-SHAKE-128s-siggen-530-30 |
| SLH-DSA-SHAKE-128s-siggen-531-30 |
| SLH-DSA-SHAKE-128s-siggen-532-30 |
| SLH-DSA-SHAKE-128s-siggen-604-30 |
| SLH-DSA-SHAKE-128s-siggen-605-30 |
| SLH-DSA-SHAKE-128s-siggen-606-30 |
| SLH-DSA-SHAKE-128s-siggen-607-30 |
| SLH-DSA-SHAKE-128s-siggen-608-30 |
| SLH-DSA-SHAKE-128s-siggen-609-30 |
| SLH-DSA-SHAKE-128s-siggen-610-30 |
| SLH-DSA-SHAKE-128s-sigver-337-30 |
| SLH-DSA-SHAKE-128s-sigver-338-30 |
| SLH-DSA-SHAKE-128s-sigver-339-30 |
| SLH-DSA-SHAKE-128s-sigver-340-30 |
| SLH-DSA-SHAKE-128s-sigver-341-30 |
| SLH-DSA-SHAKE-128s-sigver-342-30 |
| SLH-DSA-SHAKE-128s-sigver-343-30 |
| SLH-DSA-SHAKE-128s-sigver-344-30 |
| SLH-DSA-SHAKE-128s-sigver-345-30 |
| SLH-DSA-SHAKE-128s-sigver-346-30 |
| SLH-DSA-SHAKE-128s-sigver-347-30 |
| SLH-DSA-SHAKE-128s-sigver-348-30 |
| SLH-DSA-SHAKE-128s-sigver-349-30 |
| SLH-DSA-SHAKE-128s-sigver-350-30 |
| SLH-DSA-SHAKE-128s-sigver-463-30 |
| SLH-DSA-SHAKE-128s-sigver-464-30 |
| SLH-DSA-SHAKE-128s-sigver-465-30 |
| SLH-DSA-SHAKE-128s-sigver-466-30 |
| SLH-DSA-SHAKE-128s-sigver-467-30 |
| SLH-DSA-SHAKE-128s-sigver-468-30 |
| SLH-DSA-SHAKE-128s-sigver-469-30 |
| SLH-DSA-SHAKE-128s-sigver-470-30 |
| SLH-DSA-SHAKE-128s-sigver-471-30 |
| SLH-DSA-SHAKE-128s-sigver-472-30 |
| SLH-DSA-SHAKE-128s-sigver-473-30 |
| SLH-DSA-SHAKE-128s-sigver-474-30 |
| SLH-DSA-SHAKE-128s-sigver-475-30 |
| SLH-DSA-SHAKE-128s-sigver-476-30 |
| SLH-DSA-SHAKE-192f-keygen-71-30 |
| SLH-DSA-SHAKE-192f-keygen-72-30 |
| SLH-DSA-SHAKE-192f-keygen-73-30 |
| SLH-DSA-SHAKE-192f-keygen-74-30 |
| SLH-DSA-SHAKE-192f-keygen-75-30 |
| SLH-DSA-SHAKE-192f-keygen-76-30 |
| SLH-DSA-SHAKE-192f-keygen-77-30 |
| SLH-DSA-SHAKE-192f-keygen-78-30 |
| SLH-DSA-SHAKE-192f-keygen-79-30 |
| SLH-DSA-SHAKE-192f-keygen-80-30 |
| SLH-DSA-SHAKE-192f-siggen-77-30 |
| SLH-DSA-SHAKE-192f-siggen-78-30 |
| SLH-DSA-SHAKE-192f-siggen-79-30 |
| SLH-DSA-SHAKE-192f-siggen-80-30 |
| SLH-DSA-SHAKE-192f-siggen-81-30 |
| SLH-DSA-SHAKE-192f-siggen-82-30 |
| SLH-DSA-SHAKE-192f-siggen-83-30 |
| SLH-DSA-SHAKE-192f-siggen-143-30 |
| SLH-DSA-SHAKE-192f-siggen-144-30 |
| SLH-DSA-SHAKE-192f-siggen-145-30 |
| SLH-DSA-SHAKE-192f-siggen-146-30 |
| SLH-DSA-SHAKE-192f-siggen-147-30 |
| SLH-DSA-SHAKE-192f-siggen-148-30 |
| SLH-DSA-SHAKE-192f-siggen-149-30 |
| SLH-DSA-SHAKE-192f-siggen-389-30 |
| SLH-DSA-SHAKE-192f-siggen-390-30 |
| SLH-DSA-SHAKE-192f-siggen-391-30 |
| SLH-DSA-SHAKE-192f-siggen-392-30 |
| SLH-DSA-SHAKE-192f-siggen-393-30 |
| SLH-DSA-SHAKE-192f-siggen-394-30 |
| SLH-DSA-SHAKE-192f-siggen-395-30 |
| SLH-DSA-SHAKE-192f-siggen-455-30 |
| SLH-DSA-SHAKE-192f-siggen-456-30 |
| SLH-DSA-SHAKE-192f-siggen-457-30 |
| SLH-DSA-SHAKE-192f-siggen-458-30 |
| SLH-DSA-SHAKE-192f-siggen-459-30 |
| SLH-DSA-SHAKE-192f-siggen-460-30 |
| SLH-DSA-SHAKE-192f-siggen-461-30 |
| SLH-DSA-SHAKE-192f-sigver-113-30 |
| SLH-DSA-SHAKE-192f-sigver-114-30 |
| SLH-DSA-SHAKE-192f-sigver-115-30 |
| SLH-DSA-SHAKE-192f-sigver-116-30 |
| SLH-DSA-SHAKE-192f-sigver-117-30 |
| SLH-DSA-SHAKE-192f-sigver-118-30 |
| SLH-DSA-SHAKE-192f-sigver-119-30 |
| SLH-DSA-SHAKE-192f-sigver-120-30 |
| SLH-DSA-SHAKE-192f-sigver-121-30 |
| SLH-DSA-SHAKE-192f-sigver-122-30 |
| SLH-DSA-SHAKE-192f-sigver-123-30 |
| SLH-DSA-SHAKE-192f-sigver-124-30 |
| SLH-DSA-SHAKE-192f-sigver-125-30 |
| SLH-DSA-SHAKE-192f-sigver-126-30 |
| SLH-DSA-SHAKE-192f-sigver-225-30 |
| SLH-DSA-SHAKE-192f-sigver-226-30 |
| SLH-DSA-SHAKE-192f-sigver-227-30 |
| SLH-DSA-SHAKE-192f-sigver-228-30 |
| SLH-DSA-SHAKE-192f-sigver-229-30 |
| SLH-DSA-SHAKE-192f-sigver-230-30 |
| SLH-DSA-SHAKE-192f-sigver-231-30 |
| SLH-DSA-SHAKE-192f-sigver-232-30 |
| SLH-DSA-SHAKE-192f-sigver-233-30 |
| SLH-DSA-SHAKE-192f-sigver-234-30 |
| SLH-DSA-SHAKE-192f-sigver-235-30 |
| SLH-DSA-SHAKE-192f-sigver-236-30 |
| SLH-DSA-SHAKE-192f-sigver-237-30 |
| SLH-DSA-SHAKE-192f-sigver-238-30 |
| SLH-DSA-SHAKE-192s-keygen-51-30 |
| SLH-DSA-SHAKE-192s-keygen-52-30 |
| SLH-DSA-SHAKE-192s-keygen-53-30 |
| SLH-DSA-SHAKE-192s-keygen-54-30 |
| SLH-DSA-SHAKE-192s-keygen-55-30 |
| SLH-DSA-SHAKE-192s-keygen-56-30 |
| SLH-DSA-SHAKE-192s-keygen-57-30 |
| SLH-DSA-SHAKE-192s-keygen-58-30 |
| SLH-DSA-SHAKE-192s-keygen-59-30 |
| SLH-DSA-SHAKE-192s-keygen-60-30 |
| SLH-DSA-SHAKE-192s-siggen-233-30 |
| SLH-DSA-SHAKE-192s-siggen-234-30 |
| SLH-DSA-SHAKE-192s-siggen-235-30 |
| SLH-DSA-SHAKE-192s-siggen-236-30 |
| SLH-DSA-SHAKE-192s-siggen-237-30 |
| SLH-DSA-SHAKE-192s-siggen-238-30 |
| SLH-DSA-SHAKE-192s-siggen-239-30 |
| SLH-DSA-SHAKE-192s-siggen-299-30 |
| SLH-DSA-SHAKE-192s-siggen-300-30 |
| SLH-DSA-SHAKE-192s-siggen-301-30 |
| SLH-DSA-SHAKE-192s-siggen-302-30 |
| SLH-DSA-SHAKE-192s-siggen-303-30 |
| SLH-DSA-SHAKE-192s-siggen-304-30 |
| SLH-DSA-SHAKE-192s-siggen-305-30 |
| SLH-DSA-SHAKE-192s-siggen-545-30 |
| SLH-DSA-SHAKE-192s-siggen-546-30 |
| SLH-DSA-SHAKE-192s-siggen-547-30 |
| SLH-DSA-SHAKE-192s-siggen-548-30 |
| SLH-DSA-SHAKE-192s-siggen-549-30 |
| SLH-DSA-SHAKE-192s-siggen-550-30 |
| SLH-DSA-SHAKE-192s-siggen-551-30 |
| SLH-DSA-SHAKE-192s-siggen-611-30 |
| SLH-DSA-SHAKE-192s-siggen-612-30 |
| SLH-DSA-SHAKE-192s-siggen-613-30 |
| SLH-DSA-SHAKE-192s-siggen-614-30 |
| SLH-DSA-SHAKE-192s-siggen-615-30 |
| SLH-DSA-SHAKE-192s-siggen-616-30 |
| SLH-DSA-SHAKE-192s-siggen-617-30 |
| SLH-DSA-SHAKE-192s-sigver-365-30 |
| SLH-DSA-SHAKE-192s-sigver-366-30 |
| SLH-DSA-SHAKE-192s-sigver-367-30 |
| SLH-DSA-SHAKE-192s-sigver-368-30 |
| SLH-DSA-SHAKE-192s-sigver-369-30 |
| SLH-DSA-SHAKE-192s-sigver-370-30 |
| SLH-DSA-SHAKE-192s-sigver-371-30 |
| SLH-DSA-SHAKE-192s-sigver-372-30 |
| SLH-DSA-SHAKE-192s-sigver-373-30 |
| SLH-DSA-SHAKE-192s-sigver-374-30 |
| SLH-DSA-SHAKE-192s-sigver-375-30 |
| SLH-DSA-SHAKE-192s-sigver-376-30 |
| SLH-DSA-SHAKE-192s-sigver-377-30 |
| SLH-DSA-SHAKE-192s-sigver-378-30 |
| SLH-DSA-SHAKE-192s-sigver-477-30 |
| SLH-DSA-SHAKE-192s-sigver-478-30 |
| SLH-DSA-SHAKE-192s-sigver-479-30 |
| SLH-DSA-SHAKE-192s-sigver-480-30 |
| SLH-DSA-SHAKE-192s-sigver-481-30 |
| SLH-DSA-SHAKE-192s-sigver-482-30 |
| SLH-DSA-SHAKE-192s-sigver-483-30 |
| SLH-DSA-SHAKE-192s-sigver-484-30 |
| SLH-DSA-SHAKE-192s-sigver-485-30 |
| SLH-DSA-SHAKE-192s-sigver-486-30 |
| SLH-DSA-SHAKE-192s-sigver-487-30 |
| SLH-DSA-SHAKE-192s-sigver-488-30 |
| SLH-DSA-SHAKE-192s-sigver-489-30 |
| SLH-DSA-SHAKE-192s-sigver-490-30 |
| SLH-DSA-SHAKE-256f-keygen-111-30 |
| SLH-DSA-SHAKE-256f-keygen-112-30 |
| SLH-DSA-SHAKE-256f-keygen-113-30 |
| SLH-DSA-SHAKE-256f-keygen-114-30 |
| SLH-DSA-SHAKE-256f-keygen-115-30 |
| SLH-DSA-SHAKE-256f-keygen-116-30 |
| SLH-DSA-SHAKE-256f-keygen-117-30 |
| SLH-DSA-SHAKE-256f-keygen-118-30 |
| SLH-DSA-SHAKE-256f-keygen-119-30 |
| SLH-DSA-SHAKE-256f-keygen-120-30 |
| SLH-DSA-SHAKE-256f-siggen-96-30 |
| SLH-DSA-SHAKE-256f-siggen-97-30 |
| SLH-DSA-SHAKE-256f-siggen-98-30 |
| SLH-DSA-SHAKE-256f-siggen-99-30 |
| SLH-DSA-SHAKE-256f-siggen-100-30 |
| SLH-DSA-SHAKE-256f-siggen-101-30 |
| SLH-DSA-SHAKE-256f-siggen-102-30 |
| SLH-DSA-SHAKE-256f-siggen-150-30 |
| SLH-DSA-SHAKE-256f-siggen-151-30 |
| SLH-DSA-SHAKE-256f-siggen-152-30 |
| SLH-DSA-SHAKE-256f-siggen-153-30 |
| SLH-DSA-SHAKE-256f-siggen-154-30 |
| SLH-DSA-SHAKE-256f-siggen-155-30 |
| SLH-DSA-SHAKE-256f-siggen-156-30 |
| SLH-DSA-SHAKE-256f-siggen-408-30 |
| SLH-DSA-SHAKE-256f-siggen-409-30 |
| SLH-DSA-SHAKE-256f-siggen-410-30 |
| SLH-DSA-SHAKE-256f-siggen-411-30 |
| SLH-DSA-SHAKE-256f-siggen-412-30 |
| SLH-DSA-SHAKE-256f-siggen-413-30 |
| SLH-DSA-SHAKE-256f-siggen-414-30 |
| SLH-DSA-SHAKE-256f-siggen-462-30 |
| SLH-DSA-SHAKE-256f-siggen-463-30 |
| SLH-DSA-SHAKE-256f-siggen-464-30 |
| SLH-DSA-SHAKE-256f-siggen-465-30 |
| SLH-DSA-SHAKE-256f-siggen-466-30 |
| SLH-DSA-SHAKE-256f-siggen-467-30 |
| SLH-DSA-SHAKE-256f-siggen-468-30 |
| SLH-DSA-SHAKE-256f-sigver-141-30 |
| SLH-DSA-SHAKE-256f-sigver-142-30 |
| SLH-DSA-SHAKE-256f-sigver-143-30 |
| SLH-DSA-SHAKE-256f-sigver-144-30 |
| SLH-DSA-SHAKE-256f-sigver-145-30 |
| SLH-DSA-SHAKE-256f-sigver-146-30 |
| SLH-DSA-SHAKE-256f-sigver-147-30 |
| SLH-DSA-SHAKE-256f-sigver-148-30 |
| SLH-DSA-SHAKE-256f-sigver-149-30 |
| SLH-DSA-SHAKE-256f-sigver-150-30 |
| SLH-DSA-SHAKE-256f-sigver-151-30 |
| SLH-DSA-SHAKE-256f-sigver-152-30 |
| SLH-DSA-SHAKE-256f-sigver-153-30 |
| SLH-DSA-SHAKE-256f-sigver-154-30 |
| SLH-DSA-SHAKE-256f-sigver-239-30 |
| SLH-DSA-SHAKE-256f-sigver-240-30 |
| SLH-DSA-SHAKE-256f-sigver-241-30 |
| SLH-DSA-SHAKE-256f-sigver-242-30 |
| SLH-DSA-SHAKE-256f-sigver-243-30 |
| SLH-DSA-SHAKE-256f-sigver-244-30 |
| SLH-DSA-SHAKE-256f-sigver-245-30 |
| SLH-DSA-SHAKE-256f-sigver-246-30 |
| SLH-DSA-SHAKE-256f-sigver-247-30 |
| SLH-DSA-SHAKE-256f-sigver-248-30 |
| SLH-DSA-SHAKE-256f-sigver-249-30 |
| SLH-DSA-SHAKE-256f-sigver-250-30 |
| SLH-DSA-SHAKE-256f-sigver-251-30 |
| SLH-DSA-SHAKE-256f-sigver-252-30 |
| SLH-DSA-SHAKE-256s-keygen-91-30 |
| SLH-DSA-SHAKE-256s-keygen-92-30 |
| SLH-DSA-SHAKE-256s-keygen-93-30 |
| SLH-DSA-SHAKE-256s-keygen-94-30 |
| SLH-DSA-SHAKE-256s-keygen-95-30 |
| SLH-DSA-SHAKE-256s-keygen-96-30 |
| SLH-DSA-SHAKE-256s-keygen-97-30 |
| SLH-DSA-SHAKE-256s-keygen-98-30 |
| SLH-DSA-SHAKE-256s-keygen-99-30 |
| SLH-DSA-SHAKE-256s-keygen-100-30 |
| SLH-DSA-SHAKE-256s-siggen-252-30 |
| SLH-DSA-SHAKE-256s-siggen-253-30 |
| SLH-DSA-SHAKE-256s-siggen-254-30 |
| SLH-DSA-SHAKE-256s-siggen-255-30 |
| SLH-DSA-SHAKE-256s-siggen-256-30 |
| SLH-DSA-SHAKE-256s-siggen-257-30 |
| SLH-DSA-SHAKE-256s-siggen-258-30 |
| SLH-DSA-SHAKE-256s-siggen-306-30 |
| SLH-DSA-SHAKE-256s-siggen-307-30 |
| SLH-DSA-SHAKE-256s-siggen-308-30 |
| SLH-DSA-SHAKE-256s-siggen-309-30 |
| SLH-DSA-SHAKE-256s-siggen-310-30 |
| SLH-DSA-SHAKE-256s-siggen-311-30 |
| SLH-DSA-SHAKE-256s-siggen-312-30 |
| SLH-DSA-SHAKE-256s-siggen-564-30 |
| SLH-DSA-SHAKE-256s-siggen-565-30 |
| SLH-DSA-SHAKE-256s-siggen-566-30 |
| SLH-DSA-SHAKE-256s-siggen-567-30 |
| SLH-DSA-SHAKE-256s-siggen-568-30 |
| SLH-DSA-SHAKE-256s-siggen-569-30 |
| SLH-DSA-SHAKE-256s-siggen-570-30 |
| SLH-DSA-SHAKE-256s-siggen-618-30 |
| SLH-DSA-SHAKE-256s-siggen-619-30 |
| SLH-DSA-SHAKE-256s-siggen-620-30 |
| SLH-DSA-SHAKE-256s-siggen-621-30 |
| SLH-DSA-SHAKE-256s-siggen-622-30 |
| SLH-DSA-SHAKE-256s-siggen-623-30 |
| SLH-DSA-SHAKE-256s-siggen-624-30 |
| SLH-DSA-SHAKE-256s-sigver-393-30 |
| SLH-DSA-SHAKE-256s-sigver-394-30 |
| SLH-DSA-SHAKE-256s-sigver-395-30 |
| SLH-DSA-SHAKE-256s-sigver-396-30 |
| SLH-DSA-SHAKE-256s-sigver-397-30 |
| SLH-DSA-SHAKE-256s-sigver-398-30 |
| SLH-DSA-SHAKE-256s-sigver-399-30 |
| SLH-DSA-SHAKE-256s-sigver-400-30 |
| SLH-DSA-SHAKE-256s-sigver-401-30 |
| SLH-DSA-SHAKE-256s-sigver-402-30 |
| SLH-DSA-SHAKE-256s-sigver-403-30 |
| SLH-DSA-SHAKE-256s-sigver-404-30 |
| SLH-DSA-SHAKE-256s-sigver-405-30 |
| SLH-DSA-SHAKE-256s-sigver-406-30 |
| SLH-DSA-SHAKE-256s-sigver-491-30 |
| SLH-DSA-SHAKE-256s-sigver-492-30 |
| SLH-DSA-SHAKE-256s-sigver-493-30 |
| SLH-DSA-SHAKE-256s-sigver-494-30 |
| SLH-DSA-SHAKE-256s-sigver-495-30 |
| SLH-DSA-SHAKE-256s-sigver-496-30 |
| SLH-DSA-SHAKE-256s-sigver-497-30 |
| SLH-DSA-SHAKE-256s-sigver-498-30 |
| SLH-DSA-SHAKE-256s-sigver-499-30 |
| SLH-DSA-SHAKE-256s-sigver-500-30 |
| SLH-DSA-SHAKE-256s-sigver-501-30 |
| SLH-DSA-SHAKE-256s-sigver-502-30 |
| SLH-DSA-SHAKE-256s-sigver-503-30 |
| SLH-DSA-SHAKE-256s-sigver-504-30 |
Post Quantum Cryptography Support
We are actively working on implementing Post Quantum Cryptography (PQC)
support in SKC and our KMIP token for PKCS#11 as updates to the KMIP draft standard
are made. We have completed a successful KMIP interop testing these new capabilities
with multiple vendors, proving that our post quantum changes interoperate with other
vendors implementations.
New KMIP PQC Extensions supported by SKC and tested in latest interop:
- TLS 1.3 PQC Hybrid Key Agreement.
- Supports all of KMIP 3.0 Specification - Working Draft 19 - PQC Updates including new operations encapsulate, decapsulate.
New ciphers tested in interop:
- ML_KEM_512
- ML_KEM_768
- ML_KEM_1024
- ML_DSA_44
- ML_DSA_65
- ML_DSA_87
- SLH_DSA_SHA2_128s
- SLH_DSA_SHA2_128f
- SLH_DSA_SHA2_192s
- SLHDSA_SHA2_192f
- SLHDSA_SHA2_256s
- SLH_DSA_SHA2_256f
- SLH_DSA_SHAKE_128s
- SLH_DSA_SHAKE_128f
- SLH_DSA_SHAKE_192s
- SLH_DSA_SHAKE_192f
- SLH_DSA_SHAKE_256s
- SLH_DSA_SHAKE_256f
In addition we have added just over 5800 new test cases to our testing infrastructure.
A list of the test cases can be found on the Conformance tab.
Secure KMIP Client SDK Export Compliance
We have some good news regarding compliance with U.S. export controls!
P6R has obtained a Commodity Classification (Form BIS-6002L ~ CCATS No. G154787) from the Commerce Department's
Bureau of Industry and Security confirming that the SKC Secure KMIP Client SDK is classified under Export
Control Classification Number 5D002.c.1 on the Commerce Control List of the Export Administration Regulations (EAR).
As a result, SKC Secure KMIP Client SDK software now is eligible for export under the provisions of License
Exception ENC/Unrestricted, pursuant to Section 740.17(b)(3) of the EAR. As such, SKC Secure KMIP Client SDK software
may be exported and reexported to all countries except Cuba, Iran, North Korea, Syria and Sudan, subject to the standard
restrictions on end-user and end-use described in the EAR. For more information regarding the use of License Exception ENC
and other requirements of the EAR, please visit the Bureau of Industry and Security's website www.bis.doc.gov or contact
their offices directly: Bureau of Industry and Security, Washington, D.C. (202) 482-4811
If you need further assistance or have more questions about SKC Secure KMIP Client SDK's export compliance, please Contact Us.
Resources
SKC Secure KMIP Client SDK
- P6R demonstrates KMIP Client SDK?s Standards Comformance at the 2023 Interop
- A KMIP Managed Object Cache
- p6pythonkmip ? a python extension for KMIP
- P6R demonstrates KMIP Client SDK?s Standards Conformance at RSA 2019
- 2018 OASIS KMIP Client Interop Results
- Detailed differences between KMIP 1.4 and 2.0
- P6R KMIP Toolkit Introduction
- Detailed differences between KMIP 1.0 and 1.1
- Key Management with a Powerful Keystore
- P6R's PKCS 11 Provider
- Integrating KMIP, PKCS 11, and SSH
- P6R KMIP Toolkit Introduction
Licensing and Upgrades
Our "Develop Anywhere / Deploy Anywhere"™ License Highlights
- Per-product license, no per developer costs.
- Royalty free runtime. The DLLs can be redistributed royalty free with your product on any supported platforms.
- One license covers all platforms. No need to purchase a license for each platform.
- Site licenses are also available.
- Contact Sales for licensing options.
Our products and this license are designed to enable you to develop, test and deploy your solutions on any platform or
platforms (that we support) without per-seat or per-platform restrictions.
 Contact
Contact Support
Support Call For Price
Call For Price Knowledgebase
Knowledgebase Support
Support