This document was updated on 22 Feb 2014.
See the related product page SKC.
P6R has taken a unique approach in its KMIP toolkit design by supporting the translation of a KMIP binary message into a standard DOM tree. This approach builds on existing P6R technology that supports parsing JSON into DOM trees. The result is a powerful new tool that can be used for KMIP 1.0, 1.1, 1.2, and any future version of KMIP.
Our toolkit provides a layered set of APIs and applications so that a developer can select at what level or levels of abstraction he wishes to manipulate KMIP messages.
1. LAYERS
Using figure 1 above as a guide we will describe each layer of the toolkit design.
Layer 1 (the lowest layer), contains the KMIP message parser and encoder objects. All KMIP operations and key encodings are supported. At this level the developer is working with binary messages. However, this layer does not include encryption. As a separate component P6R’s encryption layer is available for use with keys, certificates and SSL.
Also at this layer is a higher level KMIP API. This higher level API supports simple operations (e.g.,Get one managed object, Locate managed object(s), Locate and Check managed object(s)).
Layer 2, is the DOM tree object. Our DOM tree contains a plugin architecture that was previously used to support XML and JSON parsers (see XSLT and XPath for JSON). We have extended this with a 3rd plugin that takes a KMIP binary message as input and calls the objects from layer 1 to populate a DOM tree. Since a KMIP message is essentially a tree of nested structures this translation is straight forward. Once the KMIP message is represented by a DOM tree a wealth of P6R technologies’ are available for use. Note, that the DOM object by itself supports the output of its contents into XML, JSON, JsonML and a KMIP binary message. In addition, our DOM tree has been extended to directly support binary nodes such as would be necessary for keys.
Layer 3, XPath 2.0 and XSLT 2.0, as we have done with JSON we have now done with KMIP. Any part of the KMIP message can be searched for and extracted using the features in the XPath 2.0 language. Also XSLT 2.0 supports transformation such as taking out just part of a KMIP message to create a new message or translating the entire message into yet another format such as SOAP. XPath is meant to be extensible allowing a developer to easily add their own XPath functions specific to KMIP (e.g., testing for a message reply or a specific batch item). Thus via XPath and XSLT our toolkit can be customized by any user.
Also at Layer 3 is P6R’s Rule Engine. The Rule Engine uses the DOM object to represent its input of “stated facts”. The Rule Engine uses XPath as part of its rule language . Thus, for example, a Rule Set could be created to implement a KMIP policy or a validation of a message’s contents. In addition, several Rule sets can be defined with a different one loaded depending on some protocol or system state.
Our KMIP toolkit includes several supporting components which include P6R’s cryptographic objects, a Keystore to save protected keys in a client or in a server, and a database object that can be used to store object attributes and configuration information. The P6R database object supports both SQLite and Postgres databases.
2. BENEFITS
There are many benefits to our approach and our software, here are just a few:
1) As with all P6R software, this toolkit supports multiple platforms: Linux, Solaris, and Windows. It also provides several language bindings such as Python, Perl, and PHP. All P6R software is written in C++.
2) Future versions of KMIP may support XML and JSON formats. Our toolkit already supports this by using existing P6R technology with KMIP specific extensions.
3) Our layered approach allows a developer to use one or more layers of abstraction to process / generate KMIP messages.
4) Add in the rest of the P6R Platform and you are more than half way to a KMIP server (e.g., SNMP support is included and easily extended). The toolkit by itself is intended for client development.
3. KMIP PROTOCOL CONFORMANCE
P6R’s KMIP client follows the standards defined in the following documents.
1) OASIS, “Key Management Interoperabilty Protocol Specification 1.0″, OASIS Standard, 15 June 2010.
2) OASIS, “Key Management Interoperabilty Protocol Specification 1.1″, OASIS Standard, 24 January 2013.
3) OASIS, “Key Management Interoperabilty Protocol Specification 1.2″, Working Draft 08, 21 August 2013.
4) OASIS, “Key Management Interoperability Protocol Test Cases Version 1.1″, Working Draft 10, 27 April 2012.
5) OASIS, “Key Management Interoperability Protocol Test Cases Version 1.2″, Working Draft 02, 06 August 2013.
6) OASIS, “KMIP Additional Message Encodings Version 1.0″, Working Draft 03, 10 August 2013.
7) OASIS, “KMIP Asymmetric Key Lifecycle Profile Version 1.0″, Working Draft 03, 10 August 2013.
8) OASIS, “KMIP Cryptographic Services Profile Version 1.0″, Working Draft 05, 10 August 2013.
9) OASIS, “KMIP Symmetric Key Foundry for FIPS 140-2 Profile Version 1.0″, Working Draft 03, 10 August 2013.
10) OASIS, “KMIP Symmetric Key Lifecycle Profile Version 1.0″, Working Draft 03, 10 August 2013.
11) OASIS, “KMIP Opaque Managed Object Store Profile Version 1.0″, Working Draft 03, 10 August 2013.
12) OASIS, “KMIP Tape Library Profile Version 1.0″, Working Draft 04a, 24 October 2013.
13) OASIS, “Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0″, Working Draft 04a, 24 October 2013.
KMIP 1.0 Operations — Client provides both synchronous and asynchronous versions of the following operations:
Create, Create Key Pair, Register, Re-key, Derive Key, Certify, Re-certify, Locate, Check, Get, Get Attributes, Get Attribute List, Add Attribute, Modify Attribute, Delete Attribute, Obtain Lease, Get Usage Allocation, Activate, Revoke, Destroy, Archive, Recover, Validate, Query (synch only), Cancel, Poll
KMIP 1.1 Operations — Client provides both synchronous and asynchronous versions of the following operations:
Create, Create Key Pair, Register, Re-key, Derive Key, Certify, Re-certify, Locate, Check, Get, Get Attributes, Get Attribute List, Add Attribute, Modify Attribute, Delete Attribute, Obtain Lease, Get Usage Allocation, Activate, Revoke, Destroy, Archive, Recover, Validate, Query (synch only), Cancel, Poll, Re-key Key Pair, Discover Versions (synch only)
KMIP 1.2 Operations — Client provides both synchronous and asynchronous versions of the following operations:
Create, Create Key Pair, Register, Re-key, Derive Key, Certify, Re-certify, Locate, Check, Get, Get Attributes, Get Attribute List, Add Attribute, Modify Attribute, Delete Attribute, Obtain Lease, Get Usage Allocation, Activate, Revoke, Destroy, Archive, Recover, Validate, Query (synch only), Cancel, Poll, Re-key Key Pair, Discover Versions (synch only), Encrypt, Decrypt, Sign, Signature Verify, MAC, MAC Verify, RNG Retrieve, RNG Seed, Hash, Create Split Key, Join Split Key
We claim conformance to the following standard defined test cases using Tag Type Length Value (TTLV), XML, and JSON message encodings for all tests:
KMIP Version 1.0 Test Cases Supported TC-311-10 Create / Destroy TC-312-10 Register / Create / Get attributes / Destroy TC-313-10 Create / Locate / Get / Destroy TC-314-10 Dual Client Test Case, ID Placeholder-linked Locate & Get Batch TC-315-10 Register / Destroy Secret Data TC-32-10 Asynchronous Locate TC-41-10 Revoke Scenario TC-51-10 Get Usage Allocation Scenario TC-61-10 Import of a Third-party Key TC-71-10 Unrecognized Message Extension with Criticality Indicator False TC-72-10 Unrecognized Message Extension with Criticality Indicator True TC-81-10 Create a Key Pair TC-82-10 Register Both Halves of a Key Pair TC-91-10 Create a Key, Re-key TC-92-10 Existing Key Expired, Re-key with Same Life-cycle TC-93-10 Existing Key Compromised, Re-key with Same Life-cycle TC-94-10 Create Key, Re-key with New Life-cycle TC-95-10 Obtain Lease for Expired Key TC-101-10 Create a Key, Archive and Recover it TC-111-10 Credential, Operation Policy, Destroy Date TC-121-10 Query, Maximum Response Size TC-131-10 Register an Asymmetric Key Pair in PKCS1 Format TC-132-10 Register an Asymmetric Key Pair and a Corresponding X509 Certificate TC-134-10 Register Key Pair, Certify and Re-certify Public KeySymmetric Key Lifecycle Profile SKLC-M-1-10 Create, GetAttributes, Destroy SKLC-M-2-10 Create, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy SKLC-M-3-10 Create, GetAttributes, Activate, GetAttributes, ModifyAttribute, Revoke, GetAttributes, Destroy SKLC-O-1-10 Create, GetAttributes, Destroy, GetAttributes
Symmetric Key Foundry for FIPS 140-2 Profile SKFF-M-1-10 Create, Destroy AES-128 SKFF-M-2-10 Create, Destroy AES-192 SKFF-M-3-10 Create, Destroy AES-256 SKFF-M-4-10 Create, Destroy DES3-168 SKFF-M-5-10 Create, Locate, Get, Destroy, Locate AES-128 SKFF-M-6-10 Create, Locate, Get, Destroy, Locate AES-192 SKFF-M-7-10 Create, Locate, Get, Destroy, Locate AES-256 SKFF-M-8-10 Create, Locate, Get, Destroy, Locate DES3-168 SKFF-M-9-10 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-128 SKFF-M-10-10 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-192 SKFF-M-11-10 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-256 SKFF-M-12-10 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-168 SKFF-O-1-10 Create, Destroy SKIPJACK-80 SKFF-O-2-10 Create, Locate, Get, Destroy, Locate SKIPJACK-80 SKFF-O-3-10 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy SKIPJACK-80 SKFF-O-4-10 Create, Destroy DES3-112 SKFF-O-5-10 Create, Locate, Get, Destroy, Locate DES3-112 SKFF-O-6-10 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-112
Asymmetric Key Lifecycle Profile Supported AKLC-M-1-10 CreateKeyPair, GetAttributes, GetAttributes, Destroy AKLC-M-2-10 CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy AKLC-M-3-10 CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy AKLC-O-1-10 CreateKeyPair, GetAttributes, Destroy, GetAttributes
KMIP Opaque Managed Object Store Profile OMOS-M-1-10 Register small opaque object OMOS-O-1-10 Register large (>10k) opaque object
KMIP Tape Library Profile Version 1.0 TL-M-1-10 Configuration TL-M-2-10 Write with new (created) key TL-M-3-10 Read an encrypted tape
Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0 SASED-M-1-10 Configuration SASED-M-2-10 Register the authentication key SASED-M-3-10 Retrieve Authentication Key
SEPATON Profile Version 1.0 SEPATON-1-10 Query SEPATON-2-10 Locate, Create SEPATON-3-10 Locate, Get, GetAttributes, Activate, GetAttributes
KMIP Version 1.1 Test Cases Supported TC-311-11 Create / Destroy TC-312-11 Register / Create / Get attributes / Destroy TC-313-11 Create / Locate / Get / Destroy TC-314-11 Dual Client Test Case, ID Placeholder-linked Locate & Get Batch TC-315-11 Register / Destroy Secret Data TC-32-11 Asynchronous Locate TC-41-11 Revoke Scenario TC-51-11 Get Usage Allocation Scenario TC-61-11 Import of a Third-party Key TC-71-11 Unrecognized Message Extension with Criticality Indicator False TC-72-11 Unrecognized Message Extension with Criticality Indicator True TC-81-11 Create a Key Pair TC-82-11 Register Both Halves of a Key Pair TC-91-11 Create a Key, Re-key TC-92-11 Existing Key Expired, Re-key with Same Life-cycle TC-93-11 Existing Key Compromised, Re-key with Same Life-cycle TC-94-11 Create Key, Re-key with New Life-cycle TC-95-11 Obtain Lease for Expired Key TC-101-11 Create a Key, Archive and Recover it TC-111-11 Credential, Operation Policy, Destroy Date TC-112-11 Device Credential, Operation Policy, Destroy Date TC-121-11 Query, Maximum Response Size TC-122-11 Query Vendor Extensions TC-131-11 Register an Asymmetric Key Pair in PKCS1 Format TC-132-11 Register an Asymmetric Key Pair and a Corresponding X509 Certificate TC-133-11 Create, Re-key Key Pair TC-134-11 Register Key Pair, Certify and Re-certify Public Key TC-141-11 Key Wrapping using AES Key Wrap and No Encoding TC-142-11 Key Wrapping using AES Key Wrap with Attributes TC-151-11 Locate a Fresh Object from the Default Group TC-152-11 Client-side Group Management TC-153-11 Default Object Group Member TC-161-11 Discover Versions TC-171-11 Handling of Attributes and Attribute Index Values TC-181-11 Digests of Symmetric Keys TC-182-11 Digests of RSA Private Keys
Symmetric Key Lifecycle Profile SKLC-M-1-11 Create, GetAttributes, Destroy SKLC-M-2-11 Create, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy SKLC-M-3-11 Create, GetAttributes, Activate, GetAttributes, ModifyAttribute, Revoke, GetAttributes, Destroy SKLC-O-1-11 Create, GetAttributes, Destroy, GetAttributes
Symmetric Key Foundry for FIPS 140-2 Profile SKFF-M-1-11 Create, Destroy AES-128 SKFF-M-2-11 Create, Destroy AES-192 SKFF-M-3-11 Create, Destroy AES-256 SKFF-M-4-11 Create, Destroy DES3-168 SKFF-M-5-11 Create, Locate, Get, Destroy, Locate AES-128 SKFF-M-6-11 Create, Locate, Get, Destroy, Locate AES-192 SKFF-M-7-11 Create, Locate, Get, Destroy, Locate AES-256 SKFF-M-8-11 Create, Locate, Get, Destroy, Locate DES3-168 SKFF-M-9-11 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-128 SKFF-M-10-11 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-192 SKFF-M-11-11 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-256 SKFF-M-12-11 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-168 SKFF-O-1-11 Create, Destroy SKIPJACK-80 SKFF-O-2-11 Create, Locate, Get, Destroy, Locate SKIPJACK-80 SKFF-O-3-11 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy SKIPJACK-80 SKFF-O-4-11 Create, Destroy DES3-112 SKFF-O-5-11 Create, Locate, Get, Destroy, Locate DES3-112 SKFF-O-6-11 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-112
Asymmetric Key Lifecycle Profile Supported AKLC-M-1-11 CreateKeyPair, GetAttributes, GetAttributes, Destroy AKLC-M-2-11 CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy AKLC-M-3-11 CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy AKLC-O-1-11 CreateKeyPair, GetAttributes, Destroy, GetAttributes
KMIP Opaque Managed Object Store Profile OMOS-M-1-11 Register small opaque object OMOS-O-1-11 Register large (>10k) opaque object
KMIP Tape Library Profile Version 1.0 TL-M-1-11 Configuration TL-M-2-11 Write with new (created) key TL-M-3-11 Read an encrypted tape
Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0 SASED-M-1-11 Configuration SASED-M-2-11 Register the authentication key SASED-M-3-11 Retrieve Authentication Key
KMIP Version 1.2 Test Cases Supported TC-311-12 Create / Destroy TC-312-12 Register / Create / Get attributes / Destroy TC-313-12 Create / Locate / Get / Destroy TC-314-12 Dual Client Test Case, ID Placeholder-linked Locate & Get Batch TC-315-12 Register / Destroy Secret Data TC-32-12 Asynchronous Locate TC-41-12 Revoke Scenario TC-51-12 Get Usage Allocation Scenario TC-61-12 Import of a Third-party Key TC-71-12 Unrecognized Message Extension with Criticality Indicator False TC-72-12 Unrecognized Message Extension with Criticality Indicator True TC-81-12 Create a Key Pair TC-82-12 Register Both Halves of a Key Pair TC-91-12 Create a Key, Re-key TC-92-12 Existing Key Expired, Re-key with Same Life-cycle TC-93-12 Existing Key Compromised, Re-key with Same Life-cycle TC-94-12 Create Key, Re-key with New Life-cycle TC-95-12 Obtain Lease for Expired Key TC-101-12 Create a Key, Archive and Recover it TC-111-12 Credential, Operation Policy, Destroy Date TC-112-12 Device Credential, Operation Policy, Destroy Date TC-121-12 Query, Maximum Response Size TC-122-12 Query Vendor Extensions TC-131-12 Register an Asymmetric Key Pair in PKCS1 Format TC-132-12 Register an Asymmetric Key Pair and a Corresponding X509 Certificate TC-133-12 Create, Re-key Key Pair TC-134-12 Register Key Pair, Certify and Re-certify Public Key TC-141-12 Key Wrapping using AES Key Wrap and No Encoding TC-142-12 Key Wrapping using AES Key Wrap with Attributes TC-151-12 Locate a Fresh Object from the Default Group TC-152-12 Client-side Group Management TC-153-12 Default Object Group Member TC-161-12 Discover Versions TC-171-12 Handling of Attributes and Attribute Index Values TC-181-12 Digests of Symmetric Keys TC-182-12 Digests of RSA Private Keys TC-PGP-1-12 Register PGP Key - RSA TC-MDO-1-12 Register MDO Key TC-MDO-2-12 Locate MDO keys by Key Value Present TC-MDO-3-12 Register MDO Key using PKCS11 URI TC-SJ-1-12 Create and Split/Join TC-SJ-2-12 Register and Split / Join TC-SJ-3-12 Join Split Keys TC-SJ-4-12 Register and Split / Join with XOR
Symmetric Key Lifecycle Profile SKLC-M-1-12 Create, GetAttributes, Destroy SKLC-M-2-12 Create, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy SKLC-M-3-12 Create, GetAttributes, Activate, GetAttributes, ModifyAttribute, Revoke, GetAttributes, Destroy SKLC-O-1-12 Create, GetAttributes, Destroy, GetAttributes
Symmetric Key Foundry for FIPS 140-2 Profile SKFF-M-1-12 Create, Destroy AES-128 SKFF-M-2-12 Create, Destroy AES-192 SKFF-M-3-12 Create, Destroy AES-256 SKFF-M-4-12 Create, Destroy DES3-168 SKFF-M-5-12 Create, Locate, Get, Destroy, Locate AES-128 SKFF-M-6-12 Create, Locate, Get, Destroy, Locate AES-192 SKFF-M-7-12 Create, Locate, Get, Destroy, Locate AES-256 SKFF-M-8-12 Create, Locate, Get, Destroy, Locate DES3-168 SKFF-M-9-12 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-128 SKFF-M-10-12 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-192 SKFF-M-11-12 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy AES-256 SKFF-M-12-12 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-168 SKFF-O-1-12 Create, Destroy SKIPJACK-80 SKFF-O-2-12 Create, Locate, Get, Destroy, Locate SKIPJACK-80 SKFF-O-3-12 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy SKIPJACK-80 SKFF-O-4-12 Create, Destroy DES3-112 SKFF-O-5-12 Create, Locate, Get, Destroy, Locate DES3-112 SKFF-O-6-12 Create, Get, Activate, Revoke, Locate, Add/Mod/Del Attributes, Destroy DES3-112
Asymmetric Key Lifecycle Profile Supported AKLC-M-1-12 CreateKeyPair, GetAttributes, GetAttributes, Destroy AKLC-M-2-12 CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy AKLC-M-3-12 CreateKeyPair, GetAttributes, Activate, GetAttributes, Destroy, Revoke, GetAttributes, Destroy AKLC-O-1-12 CreateKeyPair, GetAttributes, Destroy, GetAttributes
KMIP Opaque Managed Object Store Profile OMOS-M-1-12 Register small opaque object OMOS-O-1-12 Register large (>10k) opaque object
KMIP Tape Library Profile Version 1.0 TL-M-1-12 TL-M-1-12 Configuration TL-M-2-12 TL-M-2-12 Write with new (created) key TL-M-3-12 TL-M-3-12 Read an encrypted tape
Key Management Interoperability Protocol Storage Array with Self-Encrypting Drives Profile Version 1.0 SASED-M-1-12 Configuration SASED-M-2-12 Register the authentication key SASED-M-3-12 Retrieve Authentication Key
KMIP Cryptographic Services Profile (KMIP 1.2) Supported CS-BC-M-1-12 Encrypt with New Symmetric Key CS-BC-M-2-12 Decrypt with New Symmetric Key CS-BC-M-3-12 Encrypt and Decrypt with New Symmetric Key CS-BC-M-4-12 Encrypt with Known Symmetric Key CS-BC-M-5-12 Decrypt with Known Symmetric Key CS-BC-M-6-12 Encrypt and Decrypt with Known Symmetric Key CS-BC-M-7-12 Encrypt with Known Symmetric Key with Usage Limits CS-BC-M-8-12 Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding CS-BC-M-9-12 Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding CS-BC-M-10-12 Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC CS-BC-M-11-12 Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC and IV CS-BC-M-12-12 Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC and IV CS-BC-M-13-12 Encrypt and Decrypt with Known Symmetric Key and PKCS5 Padding and CBC and Random IV CS-BC-M-14-12 Encrypt and Decrypt with Known Symmetric Key Date Checks CS-RNG-M-1-12 RNG Retrieve CS-RNG-O-1-12 Seed RNG with Server Accept CS-RNG-O-2-12 Seed RNG with Server Partial Accept CS-RNG-O-3-12 Seed RNG with Server Ignore CS-RNG-O-4-12 Seed RNG with Server Deny CS-AC-M-1-12 Sign with Known Asymmetric Key CS_AC-M-2-12 Signature Verify with Known Asymmetric Key CS-AC-M-3-12 Sign and Signature Verify with Known Asymmetric Key CS-AC-M-4-12 MAC with Known Key CS_AC-M-5-12 MAC Verify with Known Key CS-AC-M-6-12 MAC and MAC Verify with Known Key CS-AC-M-7-12 Hash CS-AC-M-8-12 Sign and Signature Verify with Known Asymmetric Key Date Checks
KMIP Additional Message Encodings Supported (for KMIP 1.0, 1.1 & 1.2)
MSGENC-HTTPS-1-10 HTTPS POST: Query, Maximum Response Size
MSGENC-XML-1-10 Message Encoding XML: Query, Maximum Response Size (In addition, we have run all above test cases in XML mode.)
MSGENC-JSON-1-10 Message Encoding JSON: Query, Maximum Response Size (In addition, we have run all above test cases in JSON mode.)
Managed Objects Supported
Certificate, Symmetric Key, Public Key, Private Key, Split Key, Template, Secret Data, Opaque Object, PGP Key
Cryptographic Algorithms
DES, 3DES, DES-X, AES (including counter mode), RSA, DSA, DH, HMAC-SHA1, HMAC-SHA224
HMAC-SHA256, HMAC-SHA384, HMAC-SHA512, HMAC-MD2, HMAC-MD4, HMAC-MD5, Blowfish, CAST5, RC2
Key Format Types
Raw, Opaque, PKCS#1, PKCS#8, X.509, Transparent Symmetric Key, Transparent DSA Private Key
Transparent DSA Public Key, Transparent RSA Private Key, Transparent RSA Public Key
Certificate Types
X.509
Support for the Suite B Profile
This profile is defined by the document:
OASIS, “KMIP Suite B Profile Version 1.0″, Working Draft 03a, 24 October 2013. P6R’s KMIP client uses the OpenSSL library for its SSL/TLS support (see http://www.openssl.org/). Our client allows the user to select the ciphers to use for SSL/TLS via the API call:
setSSLOptions( const P6WCHAR* pCiphers, P6SECURESOCKETFLAGS fSecureFlags )
where the “pCiphers” paramter is a pointer to a NULL terminated character string containing the OpenSSL cipher command (see http://www.openssl.org/docs/apps/ciphers.html). If pCiphers parameter is NULL, then the secure default will be automatically be used: “TLSv1+HIGH:!SSLv2:!aNULL:!eNULL:!3DES:@STRENGTH” which enables SSLv3 and TLSv1, disables SSLv2, disables ciphers that do not use authentication, disables 3DES, and prefers the strongest ciphers first. The only constraint, is that the specified ciphers in the setSSLOptions API call are supported by the OpenSSL library in use, whether supplied by the customer or P6R.
4. A FEW EXAMPLES
Example 1: included below are 4 files containing the same KMIP 1.0 message. The first file is a dump of its binary bytes. The remaining files are translations into XML, JSON, and JsonML. All the translated files came from the same DOM tree.
1) kmip-binary 2) kmip-xml 3) kmip-json 4) kmip-jsonml
Example 2: as a second example the same binary KMIP message used in #1 above is manipulated by an XSLT template to generate a Tag-Text output (with some values dropped). The second file is the result of running the template on the same DOM tree generated in example 1.
Template: kmip-template1
Tag-Text result: kmip-tagtext
(Note that this template is just a very simple example of what is possible with XSLT & XPath 2.0.)
Example 3: the binary message below is generated from a KMIP test server while its XML version is an output from P6R’s KMIP client. These messages are a more complex KMIP example of a response to a KMIP Query operation.
1) binary-queryresponse 2) xml-queryresponse
5. Product Summary
The toolkit provides C++ based component libraries that currently implement the KMIP 1.0/1.1/1.2 protocols. The toolkit provides full KMIP message parsing and message generation. The toolkit provides several different layers of abstraction, each building on the previous, enabling the developer to use whichever layer or layers best suit their needs. The toolkit comes with binaries for Linux, Solaris, and Windows platforms. The toolkit supports logging of incoming and outgoing KMIP messages in XML, JSON, and JsonML to simplify development and trouble shooting.
6. Interoperability Announcements
QuintessenceLabs Announces Interoperability Partnership With P6R – Project 6 Research
Thales e-Security (Thales Alliance for Solution and Application Providers (ASAP) member)
January 2014, OASIS Interop testing with the following KMIP servers: Cryptsoft (C and Java), Dell, HP, IBM, SafeNet, Thales, and Vormetric.
P6R in the OASIS Interop booth for RSA 2014
P6R, Inc is a member of OASIS and of the KMIP Technical Committee
 Contact
Contact Support
Support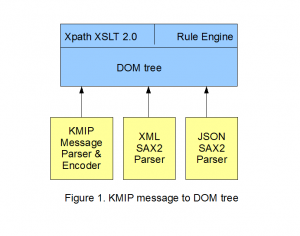
On March 4th, 2014 at 7:29 am Detailed differences between KMIP 1.0 and 1.1 | DP企业数据保护 加密安全 Andy@SafeNet said,
[…] part of the process of modifying our KMIP 1.0 protocol implementation to support the new KMIP 1.1specification we compared the two specifications and listed all of […]
Link